With the growing convergence of IT and OT, industrial systems are becoming more connected—and more vulnerable. They face risks like unauthorized access, ransomware, and supply chain attacks. To address these threats, the IEC 62443 standard series provides a comprehensive framework for securing Industrial Automation and Control Systems (IACS) including PLCs, SCADA systems, and industrial IoT devices.
IEC 62443, the global standard for industrial cybersecurity, offers a structured framework to secure Industrial Automation and Control Systems (IACS) across their lifecycle. It promotes risk-based security levels, defense-in depth strategies, and clear role definitions for stakeholders.
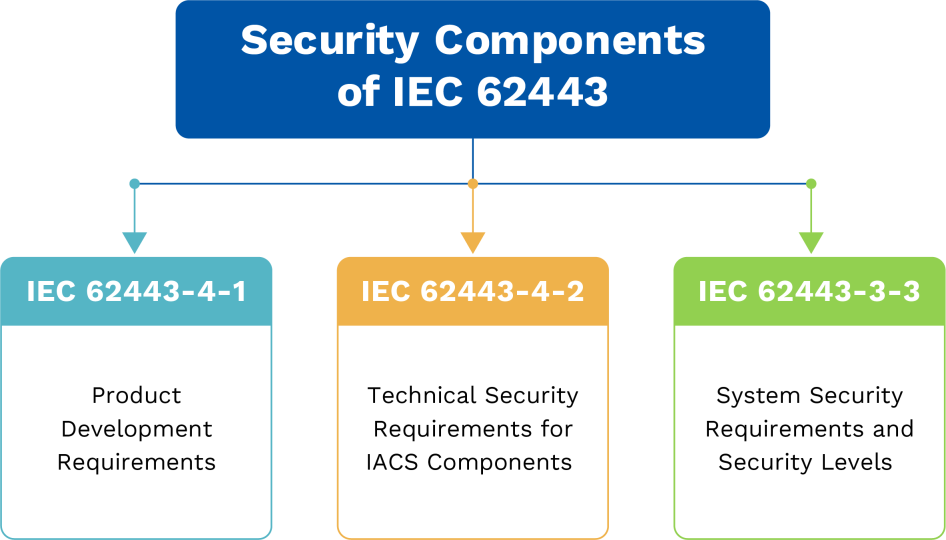
At eInfochips, we offer comprehensive industrial cybersecurity services aligned with IEC 62443-4-1, IEC 62443-4-2, and IEC 62443-3-3 standards. Our offerings include system-level risk assessments and security capability mapping (IEC 62443-3-3), secure product development lifecycle support (IEC 62443-4-1), and embedded system and component-level security hardening (IEC 62443-4-2). Whether you’re upgrading legacy systems or developing secure-by-design industrial solutions, we help ensure your products are secure, compliant, and resilient.
Single point of ownership
End to end Edge to Cloud Cybersecurity provider,
Advanced level partnerships
with Qualcomm, Nvidia, NXP focusing on Edge Cybersecurity
Core competency and
DNA
in building OT systems and related cybersecurity posture
Cybersecurity CoE
One stop shop including infra / resource / program
management with a focus on business outcomes
Cybersecurity Lab
with Dedicated Infrastructure for VAPT
Assessment Frameworks
Overall security assessment framework, Detailed Compliance assessment frameworks for CRA, RED 3, IEC 62443, ISO 21434 etc.
Schedule a 30-minute consultation with our Automotive Solution Experts
Schedule a 30-minute consultation with our Battery Management Solutions Expert
Schedule a 30-minute consultation with our Industrial & Energy Solutions Experts
Schedule a 30-minute consultation with our experts


