Denial of Service (DoS) attacks are a type of cyberattack that include Distributed Denial of Service (DDoS) attacks as a subset. In DDoS attacks, numerous Internet-connected machines, collectively referred to as a “botnet,” are employed to flood targeted websites with fictitious traffic. Unlike other types of cyberattacks, DDoS attacks do not aim to breach your security restrictions. Instead, they seek to deny authorized users access to your website and servers.
Furthermore, DDoS attacks can also be used as a cover for other nefarious behavior or to disable security features, going against the target’s security limits. The successful dispersion of service attacks is a significant development that affects all online users. This makes DDoS attacks a preferred tool for hackers, cybercriminals, and anyone else looking to advance an agenda or fight for a cause.
DDoS attacks can occur repeatedly or in small bursts. Regardless of the method, they can have long-lasting effects on a website or business. These effects can last for days, weeks, or even months as the latter tries to recover. Therefore, DDoS attacks can become extremely damaging for any online organization.
Just to give you a perspective on how big this problem is, according to Microsoft, there were an average of 1,435 attacks per day in 2022 that they were able to mitigate.
DDoS attacks can lead to various consequences such as lost sales, damage to consumer confidence, forced compensation pay-outs by companies, and long-term harm to a company’s reputation, among other things. Thus, it is essential to have a plan in place to prevent, detect, and respond to DDoS attacks to protect your business and its customers.
What is a DDoS Attack?
When attackers attempt to prevent the delivery of a service, whether by a single system or numerous systems, it is known as a Distributed Denial of Service (DDoS) attack. This attack can restrict access to servers, devices, services, networks, apps, and even specific features within applications. The attack typically involves flooding the system with data requests, which can cause service interruptions or even complete shutdowns of websites, apps, or businesses, depending on the available RAM, CPU, and internet bandwidth.
DDoS attacks pose a serious risk to many aspects of our existence, including the Internet of Things (IoT), smart cities, healthcare, information technology, and commercial components. Despite their scale, DDoS attacks continue to rise in complexity, volume, and frequency, making them a constant threat to the network security of all business units.
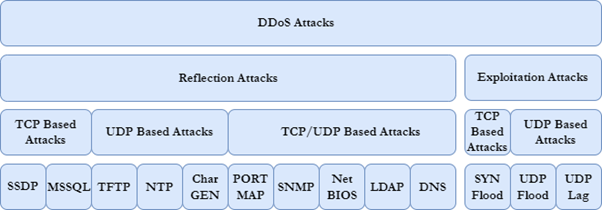
The creators of the DDoS attack divided it into two parts: the DDoS attack-based demonstration and the DDoS-based attack. The first section involves transmitting attack communication to the target as HTTP calls using Internet-connected devices while concealing the attacker’s identity. The requests are sent from the originating IP address to the display server’s IP addresses (bots), transferring all additional responsibilities to the victim. These attacks typically take advantage of system principles such as TCP, individual UDP, or integration. TCP-based attacks may employ MSSQL or SSDP, while UDP-based attacks may use CharGen, NTP, or TFTP. Validated assaults may also utilize protocols such as DNS, LDAP, NetBIOS, SNMP, or PORTMAP.
The second element of the DDoS attack is a DDoS-based attack that uses both TCP and UDP to its advantage. SYN floods are TCP-based attacks, while UDP and UDP-Lag floods are UDP-based attacks. A full DDoS attack taxonomy is depicted in the picture.
In summary, DDoS attacks are a significant threat to network security, and their complexity, volume, and frequency continue to increase. It is crucial to implement measures to prevent and mitigate the effects of DDoS attacks on businesses and organizations.
According to a CISCO analysis, the frequency of DDoS attacks is predicted to increase significantly soon. Statistics from 2023 show that the number of DDoS attacks will double from 7.9 million to 15.4 million, compared to 2017. DDoS attacks pose a severe threat to service providers due to their size and speed, with the largest reported attack being 1.7 Tb/s. Recent DDoS attacks have resulted in expensive downtime, costing up to USD 221,836.80.
DDoS attacks pose a significant risk since they can access networks, services, and corporate applications. It can be difficult to detect and repel these attacks accurately, given their similarity to non-malicious detecting issues, such as system administrators performing maintenance or technical issues across a network. Attempts to detect DDoS attacks may result in slow network performance when accessing files or when a certain website becomes inaccessible.
There are three primary categories of DDoS attacks
- Volume-Based Attacks – These attacks use a large amount of fake traffic to overwhelm an application, such as a server or a website. Examples include feed flood feed, ICMP, and UDP. The attack volume is measured in Bits Per Second (BPS).
- Protocol Attacks – During a protocol or network layer DDoS attack, numerous packets are sent to the targeted network infrastructure and infrastructure management tools. These protocol attacks, measured in Packets Per Second (PPS), include SYN and Smurf DDoS floods, among others.
- Application Layer Attacks – Various malicious programs conduct application layer attacks. The size of an application layer attack is measured in Requests Per Second (RPS).
DDOS Attack Symptoms & Tools
DDoS attacks can simulate various seemingly insignificant events that can disrupt access, such as a compromised server or system, an excessive number of legitimate requests from valid users, or a cut cable. To determine what is happening, traffic analysis is typically necessary.
DDoS attackers often employ botnets, which are networks of malware-controlled programs. Typically, desktops and servers are infected endpoints, but increasingly, more IoT and mobile devices are being targeted. Attackers prefer these endpoints by identifying vulnerable computer systems that they can infect with malicious attacks, mass-infection campaigns, and other activities like identity theft. The creators of these bots are increasingly renting them out to attackers again.
How DDOS Attacks Evolve
As mentioned briefly above, hired botnets are frequently used to carry out these attacks, and this pattern is likely to persist. Another technique is the Advanced Persistent Denial-of-Service (APDoS), which involves using several attack vectors during an attack. For instance, APDoS attacks may target the application background, including the server, as well as apps and stored data. The attack on Chuck Mackey, CEO of Binary Defense Partners, was described as “going beyond flooding.”
Furthermore, according to Mackey, attackers often misunderstand not only their targets but also the companies on whom they depend, such as ISPs and cloud providers. This is a thorough, all-encompassing attack that changes how DDoS attacks affect enterprises and raises their risk. “Firms no longer worry about the DDoS attacks themselves, but the attacks on a huge number of business partners, vendors, and suppliers of those businesses they rely on. The phrase ‘an enterprise is as secure as its weakest link’ is among the oldest in the security industry. Today, the weak link can, and frequently is, a third party, as demonstrated by recent breaches,” said Mike Overly, a cybersecurity advocate at Foley & Lardner LLP.
Of course, technology and techniques will not stop as long as attackers continue to be successful in their DDoS attacks. According to Rod Soto, Director of Security Research at JASK, this type of assault will continue to evolve with the introduction of new IoT devices, improved learning capabilities, and AI. “As soon as attackers adopt this technology, it will be far more difficult for defenders to handle DDoS attacks, especially those that bypass ACLs or basic signatures. That means that DDoS defense technologies will also need to evolve,” explained Soto.
How Cybercriminals are Harnessing AI to Supercharge DDoS Attacks
The emergence of Artificial Intelligence (AI) has created new opportunities for cybercriminals, who are integrating AI into their arsenal of tools. AI makes their attacks more powerful, sharper, and faster. Data-driven systems can now enable cybercriminals to carry out Distributed Denial of Service (DDoS) attacks that use artificial intelligence, allowing for quick decision-making, problem-solving, and even predictive defense strategies.
Evolution of DDoS attacks
- Initially, DoS tools were basic scripts that allowed attackers to modify HTTP, TCP, and UDP packets.
- To create a repetition process, developers of DoS code integrated feedback loops into these scripts, which enabled attackers to remove themselves from the equation.
- The idea of distribution was then implemented to expand and enhance the attack surface, with DDoS attackers recruiting bots to launch more powerful and harder-to-detect attacks.
- To enlarge their army, attackers turned to automated scanning, scouring thousands of networks to identify unpatched and vulnerable systems that could be infected with DoS scripts or malware to serve as bot clients.
- To manage larger attack surfaces, the concept of centralized command was introduced. Attackers now use a command-and-control center, which provides an additional layer of anonymity.
How AI Pushes More Persistence and Control to the Bots
- A fully AI-based DDoS attack removes the human DDoSer from the equation.
- It makes the source of the attack difficult to trace.
- The machine does not get tired (attacking 24*7) and has a non-existent error rate.
- AI-powered DDoS attacks enable attackers to automate repetitive tasks and anticipate outcomes, including predicting the defensive strategy.
- Such attacks can adjust their attack strategy automatically in response to the defensive side’s actions.
DDoS Challenges
DDoS attacks can be executed through various methods, such as DNS flooding, utilizing high bandwidth, and exploiting cloud resources.
Hackers are now focusing more on low-level “service malware,” which can downgrade expensive services without fully disabling them by employing DDoS techniques. In certain cases, these attacks can even prevent DDoS security systems from being detected over an extended period.
With the proliferation of IoT devices, there is a growing number of network access points that businesses can be targeted through.
To promptly and effectively prevent floods in both network and application layers, storage monitoring technologies are becoming increasingly necessary.
How to Prevent DDoS Attacks
To mitigate the risks and vulnerabilities posed by DDoS attacks, it’s essential to take several steps. Begin by identifying all the applications that are exposed to the public internet and understanding their normal behavior to detect any anomalies promptly.
Another crucial step is to secure a reliable DDoS protection service that has advanced mitigation capabilities to handle attacks of any scale. Look for services that provide traffic monitoring, adaptive real-time tuning, DDoS protection telemetry, and access to a rapid response team.
It’s also essential to develop a DDoS response strategy that includes assembling a DDoS response team with clear roles and responsibilities. The team responsible for security should possess the knowledge to detect, reduce the impact of, and supervise an attack, while also collaborating with stakeholders and customers.
In the event of an attack, it’s recommended to seek assistance from technical experts, such as an established DDoS response team, to aid in investigating and analyzing the post-attack situation. Following an attack, it is vital to conduct a retrospective analysis to identify any disturbances to the service or user experience.
This analysis will help in determining which applications or services were most impacted. Evaluate the effectiveness of the DDoS response strategy and find ways to improve it for future attacks.
Trends For 2023 And Beyond?
- Attackers will increasingly employ DDoS attacks as diversions to conceal more complex cyberattacks, such as data breaches, launched simultaneously.
- Despite being a longstanding threat, DDoS botnet attacks originating from the Internet of Things (IoT) will persist and cause substantial disruptions.
- We anticipate a surge in DDoS attacks stemming from account takeovers, wherein malicious actors illicitly obtain access to resources to launch DDoS attacks.
- Given the ongoing emergence of geopolitical tensions worldwide, hacktivists are likely to continue employing DDoS attacks as a primary cyberattack tool.
Conclusion
The scale and complexity of the IoT attack surface have consequently significantly increased. Pervasive connectivity, edge computing, and strong cloud foundation availability have enabled an exponential increase in the number of connected endpoints across industrial categories and device types. Enterprises should design, develop, implement, and manage connected goods in a secure way as privacy and security information standards, laws, and regulations grow increasingly strict across worldwide markets.
Data confidentiality and integrity will be ensured by the organization’s information security. The risk of attacks is lowered using software updates, secure credentials, device authentication, risk and compliance, appropriate encryption, secure internet networks, and cloud platforms. By using vulnerability assessment and penetration testing methods, it is possible to find weaknesses and eventually close any gaps. Lastly, this strategy helps clients install secure products in the actual world that protect their goods from DDoS attacks.
eInfochips helps businesses build, install, and manage security solutions on a worldwide scale. Threat modelling and VAPT for the device, OS or firmware, web application, mobile applications, data, and cloud workloads in accordance with OWASP, MITRE, ENISA, NIST and other security industry standards, regulations, and guidelines. Get in touch with us for your security needs.












