What is Botnet?
The word “Botnet” is jargon used in the IT industry. It is a combination of two words “Robot” and “Network”─“bot”from the robot and “net” from the network. So, what is a bot? From a botnet’s perspective,a bot is a hijacked computer or IoT device infected with bot malware and remotely controlled by a hacker, identified as the “bot-master”.The network of these infected computers and devices is called a botnet.
Botnets can contaminate almost every type of Internet-linked device or IoT device, either directly or via Wi-Fi. Smartphones, PCs, laptops, smartwatches, DVRs, smart domestic appliances, security cameras, and others ─ any of these systems or IoT devices could turn out to be the target of a botnet. These bots are also known as ‘Zombies’ of computer networks.
Devices that are part of a botnet may not show any strange actions. At least, nothing the user of that device would be able to identify without an up-to-date anti-virus. But botnets would be hazardous to the intended target when they want to attack it. Your contaminated dirt devices could end up being a part of numerous botnet attacks without your knowledge.
Let’s understand, a generic modus operandi of infecting computer and IoT devices.
- Hackers search for weaknesses in the IoT devices or systems. If a hacker found any weakness, then he/she uses malware to infect machines to create botnets, else he/she plans attacks like phishing to infect the target devices with bot malware.
- After that, these infected devices get linked to the servers owned by the hacker or the group of hackers to manage these bots. It is called the command-and-control server. These command-and-control servers are used to manage communication between hackers and their compromised machines/IoT devices.
- Now, the hacked systems can be used for any kind of attack or any malicious activity by hackers.
Stage 1: Infecting Victim device
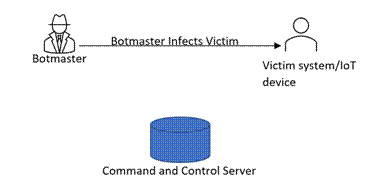
Stage 2: Infected victim device (Bot) connects to the command-and-control server
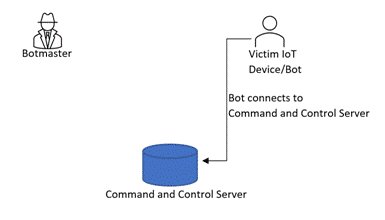
Stage 3:Botmaster indicates bots through command-and-control server

Stage 4: Bot attacks/is set to perform a task on the target system/server
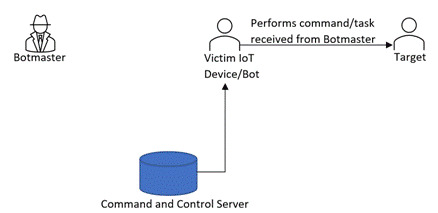
Command-and-control servers have two types of models. One, in which all the bots/IoT devices are controlled by a centralized server. Centralized servers keep the communication with all the bots and send commands to perform tasks.
Another one is distributed model, in which a botmaster sends commands to one bot, and that bot acts on that command and forwards that command to its peer bots. This process is repeated by all the bots until the entire botnet receives the command. Using one of these models, hackers conduct attacks like DoS, DDoS, and Brute-force.
What is a Botnet Attack?
A botnet attack is a big-size cyber-attack carried out by malware-contaminate dirt devices operated instantly. They have turned out to be more sophisticated, and they can also scale up their (attacker) machines to create a larger widespread attack. Invaders use botnets to compromise systems, deliver malware, and hire new devices to the brood. A botnet attack may be mostly for disruption or a means of flaming a route to introduce a secondary attack.
Most common types of botnet attacks:
- Brute Force Attack
- Distributed Denial-Of-Service (DDoS) Attack
- Spam and Phishing
- Device Bricking
- Cryptocurrency Mining
These botnet attacks mainly harm the availability of resources. The availability issues can be faced by the victim as well as the infected device itself. DDoS attacks can disrupt any server by sending too many requests at a time. This will affect the services provided by the victim servers, and legitimate users will not be able to use the resources provided by the victim server. Device bricking attacks cause a device to stop functioning, rendering it unusable.
Examples of botnet attacks:
Mirai Botnet: The IoT botnet attack exploits the insecure IoT devices with open Telnet ports and weak/default credentials to build a botnet. The victim of such attacks is IoT devices situated at remote locations without the feature to be remotely patched. To form a large botnet army, Mirai malware targets Linux-based network devices to transform them into bots. It has been used to execute major DDoS strikes including Brian Krebs’ website, French web host OVH, and Dyn cyberattack. It is used to convert insecure IoT devices into bots.
The contaminated devices then search for other vulnerable IoT devices to infect them, thus turning out to be self-propagating. The source code for Mirai was made open source by the creators. Since then, it’s been utilized to execute attacks on many IoT devices.
Last year in 2021, Cloudflare thwarted the biggest registered DDoS botnet attack that the attackers introduced with 20,000 bots in 125 countries. This was suspected to be the Mirai botnet attack.
Kneber Botnet: Itinstructed 75,000 systems from high-profile enterprises and government agencies in 2010.
There are many examples available like ZBOT/ZeuSis a bank information stealer, KOOBFACE is the most successful Web 2.0 botnet, WALEDAC is an infamous spamming bot, and Smominru, and so on.
Another use case of Botnets
Apart from being used for malicious activities, botnets can be used for many benign purposes like proctoring exams and white hat testing of systems or applications.
Several botnet service providers are available for hire who can point their botnet at your servers for an allowed time frame and volume to test your server’s capacity to manage these attacks. These facilities are often known as stressors or booters and come with various tools for observing and evaluating the outcomes.
How to avoid becoming part of botnets?
We all should consider but not be limited to the following key points to avoid becoming part of botnets. These preventing steps can help you protect your systems and Internet of Things devices.
- Always use the latest and most stable operating system on your machines/IoT devices.
- Do not open or download files from strange or unreliable sources.
- Scan all downloads before running the downloaded files or find another means of transferring files.
- Do not click on unknown or suspicious links.
- Keep your system secure by installing an antivirus program.
Businesses should be protected from such attacks because they can cause a major loss of data and revenue. Organizations can implement some best practices in their day-to-day business regime and can be secure from such attacks. As always, preventive measures should be implemented.
- Most important thing is to deploy secured products.
- Monitor traffic on your network for any unusual activities.
- Monitor login attempts with wrong credentials. Establish a standard and look out for spikes.
- Another technique is a honeypot of IoT Devices/systems to fool incoming bots.
- Set up a Web Application Firewall to block bots from specific IPs.
- Some cloud-based solutions are present that identify and block familiar and unfamiliar bots in milliseconds, irrespective of how significantly they switch their IP or how perfectly they forge their fingerprints.
eInfochips provides end-to-end IoT solutions and services for the secure development of your products. We add multiple layers of security practices in the product development lifecycle. We follow a secure by-design approach to safeguard products from roots. We integrate security workflow in your product development life cycle, which includes everything from secure by design to VAPT testing. This approach ultimately helps customers to deploy secured products in the open world that helps protect products from botnet malware.
eInfochips has helped companies develop, deploy, and manage security products at a global scale by securing their connected device networks across device-connectivity-application layers using strategic, transformational, and managed operations approach. We have 360-degree Cybersecurity expertise for threat modeling and VAPT across devices, OS/firmware, web/mobile applications, data, and cloud workloads that support security industry standards, regulations, and guidelines like NIST, ENISA, OWASP, MITRE, and IoT Security Foundation.











