Thick clients are being referred to by many names: Fat, Rich, or Heavy Clients. It follows a client-server architecture and can be developed using different programming languages like JAVA, C/C++, and .NET among others.
Vulnerability Assessment and Penetration Testing (VAPT) for thick clients includes client-side analysis, server-side analysis, and network traffic analysis.
Thick client applications can operate without a network connection. To test these applications, you have to understand the entry points for user inputs, application architecture, technologies being used, any propriety protocols, programming languages, and frameworks being used in building it.
Types of Architecture in Thick Client Applications
Two-tier thick client application
The two-tier architecture is generally found in the legacy application, for example, the .NET application communicating with the database using its connection available through an open-source. In this type of architecture, we have the client and the server. The application gets installed on the end user’s system (client) and from there it communicates with the database residing on the server.

Three-tier thick client application
As described in the image below, we have the application server that acts as a mediator between the client and the database. This communication uses the HTTP/HTTPS protocol. A few examples of this type of application are Burp suite, zap proxy, and so on.

How should thick client apps be tested?
Thick client applications are more involved and specialized than online or mobile apps, they require a unique approach to penetration testing.
When dealing with a thick client application, the first step is to acquire information, such as:
- Determining which technologies are utilized on both the client and server sides.
- Understanding the application’s functioning and behavior.
- Identifying all possible entry points for user input.
- Understanding the application’s key security protocols.
- Detecting typical flaws in languages and frameworks.
Tools Used to Test Thick Client Applications:
There are a lot fewer tools available for evaluating thick clients than there are for testing web-based programs. Many tools are no longer actively developed, while others have been migrated to online/mobile contexts.
These are the tools used for testing thick client applications:
1. Echo Mirage: It is an all-rounder testing tool for thick clients. Echo Mirage, like Burp / OWASP Zap, enables the interception of client-server traffic.
2. Sysinternals Suite: This complete collection of tools from Microsoft allows testers to view what operations are launched by the thick client application as well as the catalog entries made or acquired by the thick client. Procmon and Regmon are two popular Sysinternals utilities for checking processes and registry entries.
3. Mallory: This Linux-based utility is capable of capturing TCP/UDP communication.
4. dnspy / Dot Peek / .Net Reflector: Net-based thick clients may have hardcoded data or source code that is not obfuscated. DLL deobfuscation and inspection are possible using dnSpy and Dot Peek. .Net Reflector is a commercial program for decompiling and correcting DLLs.
5. Burp Invisible Mode: Burp includes an invisible mode that allows it to capture traffic from proxy-inadvertent thick clients.
6. Java Snoop: This allows Java thick clients to intercept any method in the JVM. Java Snoop operates on the current Java operation by connecting itself to the ongoing process.
7. Text Editors: Thick clients typically use configuration files saved in plain text on the local system, commonly as .config or .ini files. Text editors are useful for searching these configuration files for sensitive information such as hardcoded passwords, access tokens and keys, and so on.
8. Ollydbg / IDA Pro: This tool is useful for replicating EXE and DLL files. Other tools that might be handy when looking for strings or keywords are Hex Editors and Strings.
9. Nmap: This is useful for checking thick client ports.
10. Spy++: This comes with Visual Studio and also used to mitigate with the GUI.
Thick Client Vs Thin Client
| Thick Client | Thin Client |
| A thick client performs the bulk of processing between the client/server applications. | A thin client application is web-based and almost all processing is being done at the server’s side. |
| App Data is stored locally within the client’s system, where the app is installed. | Data is stored in servers. |
| The thick client application can work on a slow network connection. | The network connection must be fast. |
| The deployment in a thick client is tough and expensive. | The deployment is simpler in a thin client. |
| The data processing and validation are done on the client’s side. | Data verification is being taken care of on the server’s side. |
| The thick client application uses computer resources and consumes local resources heavily. | It consumes very less resources. |
Thick client methodology for conducting VAPT assessments
We will be focusing on the areas that are mentioned in the OWASP Windows Binary Executable Files Security Checks Project.
https://wiki.owasp.org/index.php/OWASP_Windows_Binary_Executable_Files_Security_Checks_Project
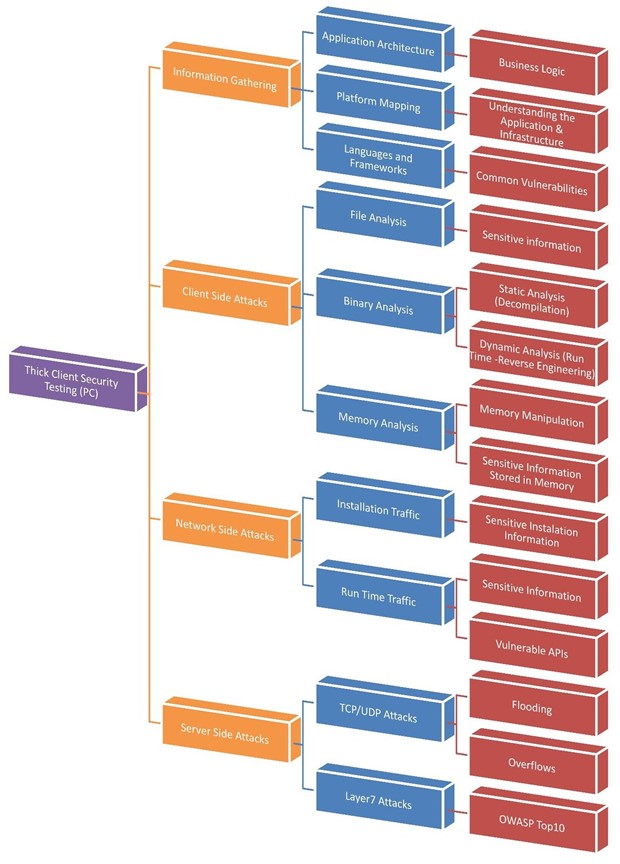
Phases in thick Client application pen testing
Information Gathering
In this phase, we need to gather details about the application. This will help us understand the functionality and architecture of the application. Essentially, we must navigate through all the UI elements with different users, each with different roles and permissions.
We should collect the information given below about the application
- Application Architecture
- Platform Mapping
- Languages and Frameworks
The set of static tools that can be used in this phase to gather information about the application is
- CFF Explorer – https://ntcore.com/?page_id=388
- PEid – https://www.aldeid.com/wiki/PEiD
- Detect It Easy (DIE) – https://github.com/horsicq/Detect-It-Easy
- Strings – https://docs.microsoft.com/en-us/sysinternals/downloads/strings
Here are the decompiler tools for .NET
- NeonFuscatorDeobfuscator – https://github.com/NotPrab/.NET-Deobfuscator
- dnSpy – https://github.com/dnSpy/dnSpy
- ILSpy – https://github.com/icsharpcode/ILSpy
- de4dot – https://github.com/de4dot/de4dot
Client-Side attacks
Files Analysis
In this phase, we must look for the local files and the registry that the applications store. Essentially, our objective is to find sensitive information such as usernames, passwords, connection strings, and API keys.
Tools that can be helpful for file analysis are:
- Process Monitor – https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
- Process Explorer – https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer
- Process Hacker – https://processhacker.sourceforge.io/
- Regshot – https://sourceforge.net/projects/regshot/
- DLLSpy – https://github.com/cyberark/DLLSpy
- Robber – https://github.com/MojtabaTajik/Robber
Binary Analysis
By the beginning of this phase, we must have gotten access to the source code of the thick client application under assessment.
Now, we must start probing and thoroughly looking at the whole code keeping in mind that we have to scout for sensitive information in the code, which might be hard-coded username or passwords, API details, API keys, endpoints, comments, and hidden functions.
Below are the tools used in this phase:
- Frida – https://github.com/frida/frida-python
- UPX Decompression – https://upx.github.io/
- PE Explorer – http://www.heaventools.com/overview.htm
- x64dbg – https://x64dbg.com/
- Luyten – https://github.com/deathmarine/Luyten
- JD-GUI – https://github.com/java-decompiler/jd-gui
- Bytecode Viewer – https://github.com/Konloch/bytecode-viewer
- ILSpy – https://github.com/icsharpcode/ILSpy
Memory Analysis
It is vital to perform memory analysis during its dynamic state. We must probe and look at the data that is getting stored in the application’s memory. If the application is developed in a two-tier architecture, then it transfers sensitive information like database connection strings and user credentials to the memory.
This is a design flaw in all the thick client applications that are developed using the two-tier architecture and it is the default behavior.
Here are the tools that are used for the assessment in this phase:
- Winhex (for windows it shows real-time registry, file system, and processes) – https://www.x-ways.net/winhex/index-m.html
- Volatility (framework used for the extraction of digital artifacts from volatile memory (RAM)) – https://github.com/volatilityfoundation/volatility
- Process Explorer – https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer
- Strings- https://docs.microsoft.com/en-us/sysinternals/downloads/strings
Now, to intercept the traffic between the thick client application and the server or database, we should use any proxy tool like burp suite. The proxy tool acts as middleware and helps us to intercept the traffic and change/update the data in transit.
Before we start intercepting the thick client application traffic, we should be aware of the difference between the following:
Non-proxy-aware
In this case, the thick client application neither has any settings to configure proxy nor has any support to proxy. For such kinds of applications, we need a different approach to set up a proxy.
We can use the burp suite and configure a proxy listener and then intercept the traffic.
Proxy aware
Here, the application itself has proxy setting options that can be used to set up the proxy and intercept the traffic using a proxy tool like burp suite.
Examples of the proxy-aware thick client are ─ Firefox, Google Chrome, and many more.
Network Side Attacks
- Installation Traffic
- Run Time Traffic
Installation Traffic and Run Time Traffic
Analyzing the network traffic between the thick client application and the server might reveal sensitive and unencrypted data like credentials, API keys being transmitted in clear-text, API endpoints, web services, proprietary protocols and file blocks sent over the wire.
Below is the set of network sniffers tools that can be used to analyze the network traffic:
- Wireshark
- SmartSniff
- tcpdump
- Microsoft Network Monitor 3.4
Server-Side Attacks
In this phase, all the OWASP TOP10 vulnerabilities should be checked.
- A01:2021-Broken Access Control
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures
- A10:2021-Server-Side Request Forgery
Conclusion
Most of the low-hanging fruits can be addressed if an organization follows secure SDLC practices, integrating security tools in the SDLC life cycle. This way the vulnerabilities are remediated at an early stage of development. Always follow the security by a design approach that ensures your project is secure from the start to the finish.
How eInfochips can help
At eInfochips, we have a dedicated team of security professionals, who have vast experience in various domains of cybersecurity. We have already helped multiple clients in transforming their security posture and reducing their risk. Our experts can help you identify your security loopholes and suggest the best approach to fix them efficiently. Get in touch with us for your security needs.












