What is SOAR?
An approach to cybersecurity known as security orchestration, automation, and response (SOAR) combines several security technologies to increase the efficacy and efficiency of incident response procedures.
Intrusion Detection and Prevention Systems (IDPS), Endpoint Detection and Response (EDR) programs, Security Information and Event Management (SIEM) systems, and other security tools are commonly integrated with SOAR platforms. Additionally, SOAR platforms can recognize and react to security risks more rapidly and precisely by utilizing artificial intelligence and machine learning.
Tracking the status of response operations and managing incident response activities are made easier with SOAR platforms. Through incident response activity audit trials and documentation, they can also help organizations meet regulatory requirements. In general, SOAR technologies lower the risk of data breaches and other security issues while assisting organizations in strengthening their incident response capabilities.
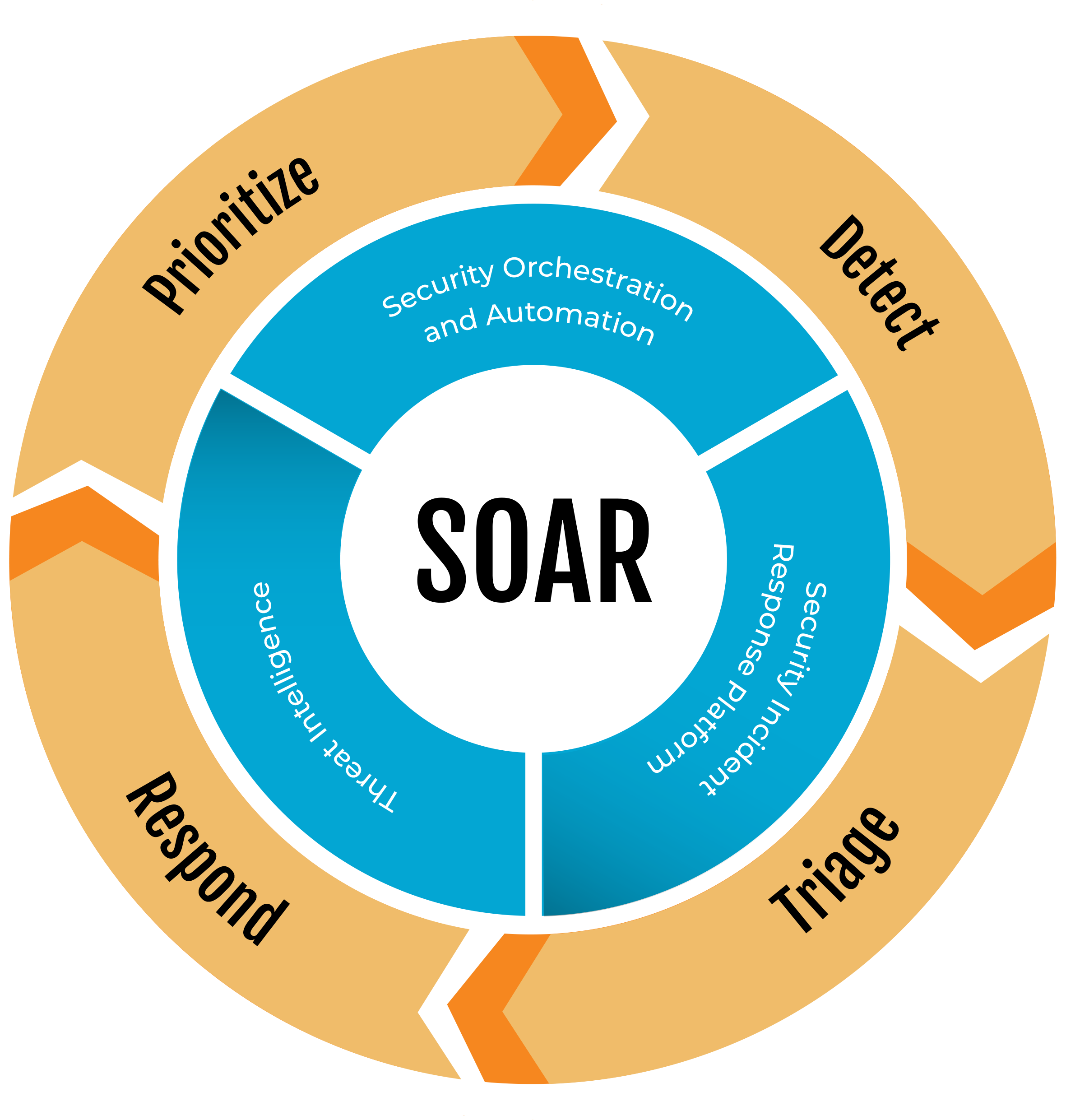
What is the Purpose of SOAR?
The term “SOAR” describes technology that businesses gather information about security threats and react to security incidents with little to no help from humans. As a result, the strain on security operations teams is greatly lessened. SOAR mitigates several significant obstacles that these teams encounter, such as:
- Ensuring that all systems are operating simultaneously and with the same efficiency.
- Acquiring and establishing the required information to distinguish between real threats and false positives.
- Arranging suitable corrective action to address risks.
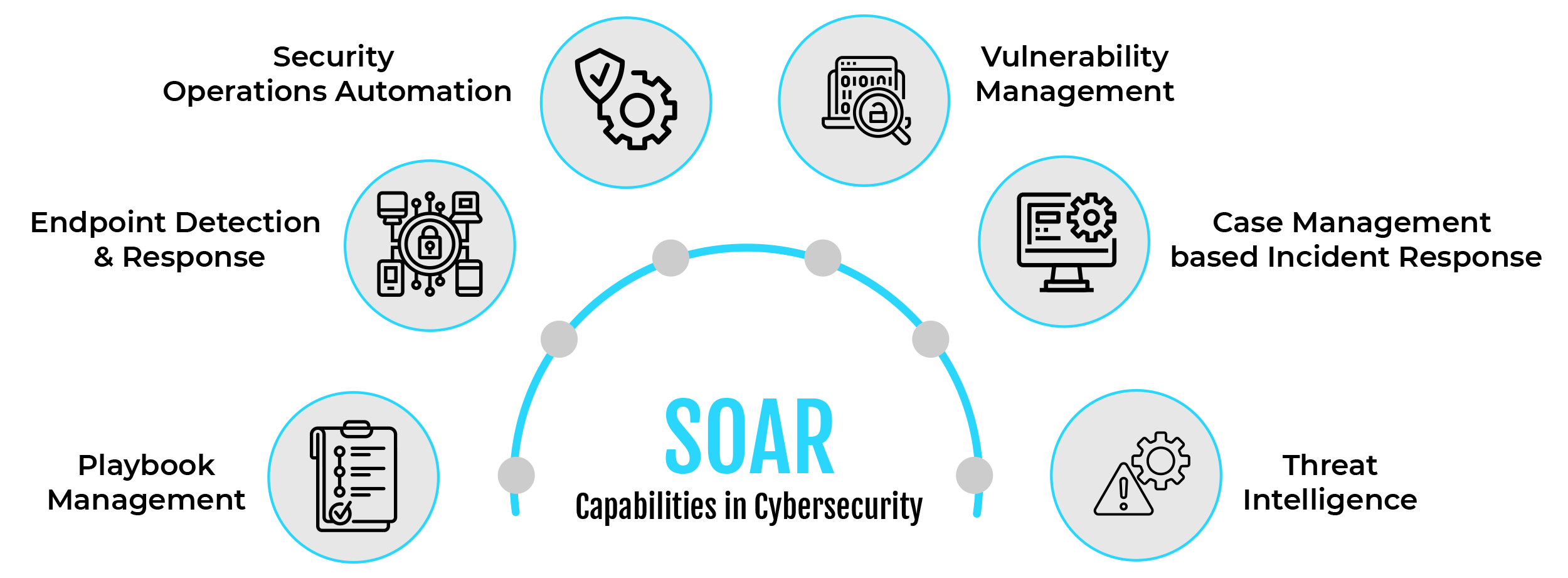
What is Included in SOAR?
- Security incident response
Technologies that facilitate incident response management, tracking, and coordination aid in the support of scalable and repeatable operations. - Threat intelligence data enrichment
Businesses can find and address vulnerabilities in their systems and networks with the use of technologies for threat and vulnerability management. This enables them to react to any threats more quickly and intelligently. These tools assist in confirming that incidents have been appropriately handled and priorities which vulnerabilities require immediate attention. In general, they improve a company’s security and readiness to combat online attacks. - Security controls automation and orchestration
Technologies for security orchestration and automation facilitate the automation and orchestration of workflows, procedures, and reporting in addition to connecting and streamlining a variety of tools.
What is SIEM and how does it relate to SOAR?
A sort of security software known as SIEM (Security Information and Event Management) offers real-time network-wide monitoring, correlation, and analysis of security-related events.
SIEM systems gather information from a variety of sources, including servers, network devices, logs, apps, and security appliances. Post that, the system aggregates and normalizes the data to present a unified picture of security-related occurrences throughout the network. This makes it possible for security analysts to recognize security events and take prompt, efficient action in response.
SIEM vs SOAR
Though there are several parallels between SIEM and SOAR systems, their functions are distinct. While SOAR focuses on automating and coordinating incident response procedures to increase the efficacy and efficiency of security operations, SIEM is concentrated on the real-time monitoring, correlation, and analysis of security events. With SOAR’s automated incident response and management capabilities and SIEM’s real-time monitoring and alerting, both technologies may be combined to create a comprehensive security plan.
SIEM, as previously mentioned, is a security system that gathers and combines information from several sources to notify and alert security analysts to possible security events.
However, to enable quicker and more effective incident response, SOAR is a security platform that offers a framework for integrating security technologies, automating security procedures, and orchestrating security workflows. To help security teams handle and react to security issues more skillfully, SOAR solutions often combine automation, orchestration, and case management features.
Key Benefits
Faster incident response: By automating incident response operations and cutting down on the time needed to detect and address security incidents, security orchestration helps security teams respond to incidents more swiftly.
Enhanced cooperation: By offering a consolidated perspective of security operations, security orchestration platforms facilitate easier information sharing and better teamwork between various teams.
Improved visibility: Security teams can identify and address threats more skillfully because of security orchestration, which gives them a thorough picture of security events and incidents throughout an organization’s network.
Decreased manual tasks: Security orchestration automates manual tasks, relieving security personnel of some of their workload and freeing them to concentrate on more difficult assignments.
Conclusion
For post-event audits and more proactive security procedures, SOCs can also make use of SOAR capabilities. Security teams can prevent similar risks in the future by using SOAR dashboards to analyze how a specific threat entered the network. Similarly, security teams may utilize SOAR data to pinpoint undetected persistent threats and target specific areas with their threat-hunting activities.
https://www.ibm.com/topics/security-orchestration-automation-response












