Operational Technology systems are the engines that run industrial facilities and critical infrastructure. These systems are designed to reliably and safely control physical or industrial processes and are used in a wide range of industries, including oil and gas, electricity, food and beverage, pharmaceutical, automotive, and manufacturing.
What is OT Security?
Operational technology (OT) security refers to the measures taken to protect systems and networks that control physical processes, such as industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. These systems are often controlled by human operators, making them vulnerable to security risks such as operator error, lack of awareness, and bypassing of security controls. With the increasing connectivity of OT systems to the internet and other networks, they have become more susceptible to cyber-attacks and remote exploitation of vulnerabilities. It is important to take proactive measures to secure these systems in order to protect against potential misuse.
In recent years, there have been several high-profile attacks that have targeted operational technology (OT) systems, such as the Stuxnet worm that was used to sabotage Iranian nuclear centrifuges and the NotPetya malware that disrupted operations at the Maersk shipping company. These incidents demonstrate that OT systems are increasingly being targeted by malicious actors, highlighting the need for security teams to be aware of the unique risks that these systems pose.
OT systems are often critical to the operation of critical infrastructure, which means that an attack on these technologies could have a significant impact. For example, an attacker could use industrial control systems (ICS) to disable the power grid or contaminate the water supply, causing significant safety, environmental and financial impacts.
Operational technologies often use proprietary protocols, which can make it difficult to secure these technologies. This is because it can be difficult to understand or reverse-engineer these protocols, making it challenging to identify and address vulnerabilities. Therefore, it is important for security teams to work closely with vendors and industry experts to better understand these protocols and develop effective security measures.
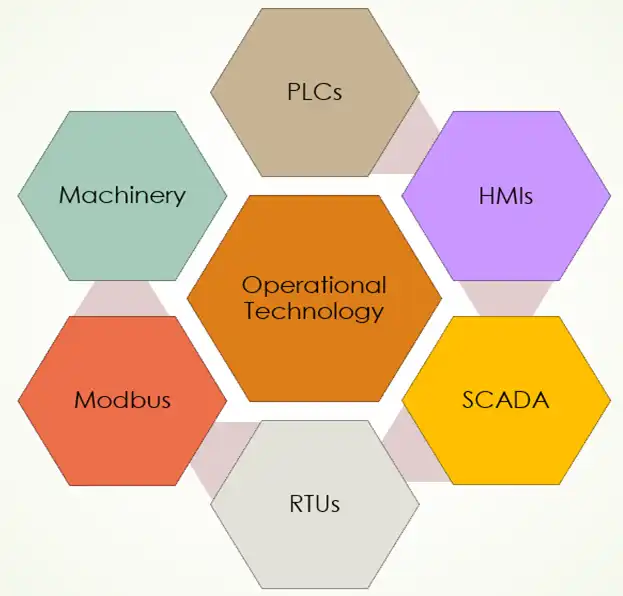
Examples of operational technologies
- SCADA – Supervisory Control and Data Acquisition systems monitor the processes of multiple machines and provide real-time information on the operator interface. The machines are monitored by PLCs, and the processes are monitored by SCADA.
- PLC – Plant control systems based on Programmable Logic Controllers (PLCs) are designed to be operated by a touch screen interface. They control and monitor the processes of multiple machines. The PLC system is modular, and operators can add and remove machines to the system without requiring changes in the PLC code.
- HMI – Human Machine Interfaces (HMIs) are used to make the interaction between humans and machines as simple and efficient as possible. HMIs are mostly used in industrial processes. The term Human Machine Interface can apply to any system that allows interaction between a user and a device.
- RTU – Remote Terminal Units (RTUs) are devices that can be connected to PLCs and provide some measure of remote access. They are often equipped with their own power supply, making them ideal for use in remote locations. RTUs can be used to monitor and control PLCs, as well as to provide data logging and other functions.
- Modbus – Modbus is a communication protocol for connecting industrial electronic devices. It is used for connecting electronic devices that use the Modbus communication protocol.
There are several factors that make OT systems more vulnerable to attack than IT systems.
- Many OT systems are legacy systems that were not a priority when they were created. This can make it difficult to deploy security controls, such as firewalls, and to patch vulnerabilities.
- OT systems are often connected to the internet, which provides attackers with a potential threat for attack. In some cases, these systems may even be directly exposed to the internet without any security controls in place.
- OT systems are controlled by proprietary protocols like DNP3, Modbus, profibus, LonWorks, and DALI which security personnel are unfamiliar with. As a result, it could be difficult to identify and stop attacks on these systems.
- OT systems are frequently essential for the smooth operation of industrial operations. This means that an attack on an OT system could have a significant impact on safety or the environment, which can make them attractive targets for attackers.
OT security challenges that organizations need to address
- Ensuring the confidentiality of data and systems
- Increasing protection against unauthorized access and malicious activity
- Minimizing the impact of security related incidents on business operations
- Ensuring the availability of data and OT systems
- Managing and improving the security of OT systems and networks
- Implementing security controls in the operational technology systems and networks
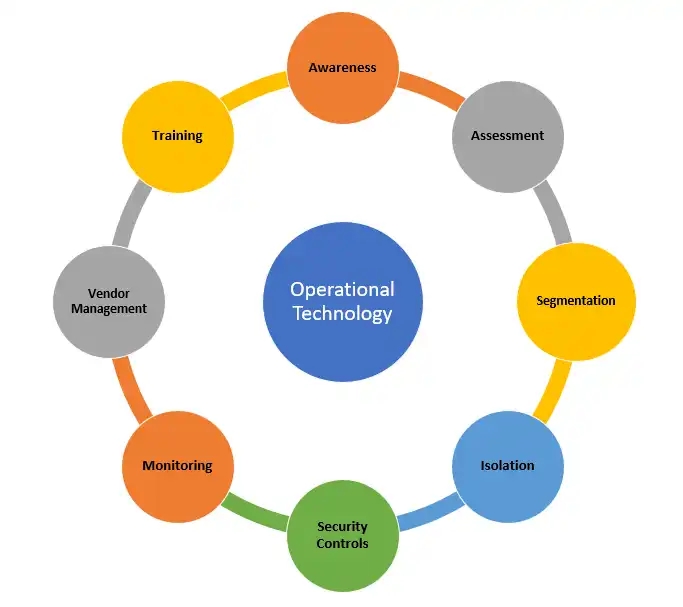
There are several steps that organizations can take to improve the security of operational technologies
- Awareness – It is crucial for security teams to increase their awareness of the unique risks associated with operational technologies, as they are often overlooked
- Assessment – Organizations should assess the security of their operational technologies. This assessment should identify the technologies that are most critical to the organization and the risks they pose.
- Segmentation – Operational technologies should be segmented from the rest of the network. This segmentation makes it more difficult for attackers to reach these technologies.
- Isolation – Operational technologies should be isolated from the internet and other networks. This isolation makes it more difficult for attackers to reach these technologies.
- Security controls – Operational technologies should be protected by security controls, such as firewalls and intrusion detection systems.
- Monitoring – Organizations should monitor their operational technologies for signs of attack. This monitoring can be used to detect attacks and respond to them quickly.
- Vendor management – Organizations should manage their relationships with vendors of operational technologies. This management should include regular communication about security vulnerabilities and patching schedules.
- Training – Operators of operational technologies should be trained in security best practices. This training will help them understand the importance of security and how to apply it.
From eInfochips
The security of operational technology (OT) devices is crucial for any organization. It is important for an organization to have security measures in place for their OT devices in order to protect its assets, data, and infrastructure from potential threats. By implementing security measures, an organization can reduce the likelihood of a successful attack and minimize the impact of an incident if one does occur.
eInfochips has helped companies manage security products on a global scale by securing their connected device networks across device-connectivity-application layers using strategic, transformational, and managed operations approaches. We have 360-degree cybersecurity expertise for threat modeling and Vulnerability Assessment and Penetration Testing (VAPT) across OT/IoT devices, OS/firmware, web/mobile applications, data, and cloud workloads that support security industry standards, regulations, and guidelines like NIST, ENISA, OWASP, MITRE, and the IoT Security Foundation. Get in touch with us to secure your operations in the most efficient manner.