Introduction
IoT devices have become an essential part of our daily routine, enabling smart-home solutions, industrial automation, healthcare applications, and much more. However, this widespread adoption also brings forth significant security challenges. Firmware plays a critical role in ensuring proper functionality and security. In this blog, we will delve into the importance of firmware security in IoT devices and explore best practices to protect these devices from potential cyber threats.
Role of Firmware security in IoT Devices
Firmware security is a critical aspect of ensuring the overall security of IoT (Internet of Things) devices. Since IoT devices are connected to the internet and often perform sensitive tasks, any vulnerabilities in their firmware can lead to severe consequences, including data breaches, privacy violations, and even physical harm if the devices control critical infrastructure.
The software and hardware are connected through firmware to an IoT device, enabling communication and control of various functionalities. It manages device operation, facilitates data exchange with backend servers, and ensures seamless user experiences. Consequently, any vulnerability in the firmware could lead to disastrous consequences, ranging from data breaches to physical damage.
Common Firmware Security Challenges in IoT Devices
- Inadequate Encryption: Firmware might lack proper encryption mechanisms, making it susceptible to eavesdropping and unauthorized access.
- Vulnerable Authentication: Weak or hardcoded credentials in the firmware, attackers might take advantage of it, in order to get unauthorized access.
- Lack of Update Mechanisms: The absence of secure update mechanisms makes it challenging to patch vulnerabilities and leaves devices exposed to known threats.
- Tampering and Alteration: Firmware without secure boot and update processes can be easily tampered with, leading to the installation of malicious code.
- Insider Threats: Insecure firmware development practices could allow malicious insiders to inject vulnerabilities into the code.
Best Practices for Firmware Security in IoT Devices
- Secure Development Lifecycle: Implementing a secure software development lifecycle (SDLC) is crucial for ensuring that security is an integral part of the entire firmware development process. Security measures must be integrated throughout the entire development process.
- Secure Development Practices: Use secure coding methods throughout the while developing process of firmware. This entails utilizing secure libraries, validating input, following code conventions, and narrowing the attack surface.
- Code Testing and Code Reviews: Periodic code reviews and thorough testing are critical for finding and correcting security flaws in firmware. Code reviews entail numerous developers thoroughly examining the firmware codebase to discover logic problems, vulnerabilities, and compliance with secure coding guidelines.
- Secure Boot and Update: Secure boot is a process that ensures only trusted and digitally signed firmware can be loaded and executed on the device. It prevents unauthorized or tampered firmware from running and safeguarding the device from malware injection during startup. Secure over-the-air (OTA) updates are crucial for delivering patches and security updates to deployed IoT devices. They should be implemented securely to prevent man-in-the-middle attacks or unauthorized modifications during the update process.
- Regular Updates and Patches: Establish a mechanism for delivering firmware updates and security patches. This will ensure that devices receive updates in a timely manner to address newly found vulnerabilities.
- Cryptographic Controls: Encryption plays a vital role in protecting sensitive data and ensuring firmware integrity. It should be used to protect data on the device side as well as in transit (when communicating with backend servers). Firmware upgrades are authenticated and verified for integrity using digital signatures. When the device receives an update, it can verify the signature to ensure it is unaltered and originates from a reliable source.
- Trusted Platform Module (TPM): Inclusion of TPM chips can enhance the security of IoT devices by providing hardware-based cryptographic functions and secure storage for sensitive data.
- Device Identity and Authentication: To avoid unwanted access, make sure every device has a distinct identity and put robust authentication procedures in place.
- Least Privilege: Implement the principle of least privilege, granting only the necessary permissions to firmware components and processes.
- Secure Credential Management: Avoid using default or hardcoded credentials in firmware, as attackers can easily discover them and gain unauthorized access. Instead, implement strong authentication mechanisms such as multi-factor authentication to enhance security. Encourage users to change default passwords during the initial setup of the IoT device to prevent potential attacks based on known credentials.
- Logging and Monitoring: Live tracking and logging allow for quick detection and response to security incidents. By analyzing logs, security teams can recognize anomalies, unwanted access attempts, and suspicious activity. Implement alert mechanisms to notify administrators of any potential security breaches or abnormal behaviors.
- Network Security: Implement robust encryption protocols like TLS (Transport Layer Security) for secure communication between IoT devices and backend servers.
- Physical Security Measures: Safeguard physical access to firmware components, preventing unauthorized tampering.
- End-of-Life Disposal: Establish proper procedures for securely decommissioning and disposing of IoT devices to prevent data exposure and potential attacks.
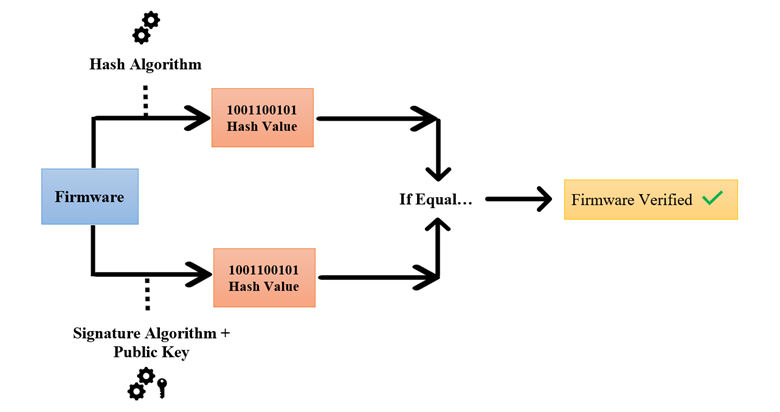
Firmware Signing Process
Firmware signing is a widely used method for enhancing firmware security in IoT devices and other embedded systems. It entails tagging the firmware image with a digital signature prior to distribution or installation on the device.
The process of firmware signing involves the following steps
- Hashing: The first step is to generate a cryptographic hash of the firmware image. The whole firmware file is input into a cryptographic hash function, which generates a fixed-size output called the hash value or digest. The hash algorithms SHA-256 and SHA-3 are frequently employed.
- Private Key Generation: A private/public key pair is generated using asymmetric encryption algorithms, such as RSA or ECC (Elliptic Curve Cryptography). The private key is kept securely by the firmware developer or the device manufacturer, while the corresponding public key is embedded in the device’s firmware or trusted boot-rom.
- Signing: Using the private key, the cryptographic hash of the firmware image is encrypted, creating the digital signature. This signature is unique to the specific firmware image and the private key used to create it.
- Embedding the Signature: A signed firmware binary is created by appending the digital signature to the firmware image.
- Firmware Verification: During the firmware update or boot process, the device checks the integrity of the firmware by performing the following steps:
- Hashing: The device calculates the cryptographic hash of the received firmware image.
- Signature Verification: Using the embedded public key (which is trusted), the device decrypts the digital signature from the firmware image.
- Comparing Hashes: The device contrasts the hash which was calculated with the hash that was decrypted from the signature. If they coincide, it means that since the firmware image was signed using the private key, it hasn’t been changed.
Conclusion
By adhering to these best practices and maintaining a proactive approach to firmware security, IoT device manufacturers can reduce the risk of cyberattacks and safeguard the privacy and safety of users and data. A single vulnerability in the firmware can have far-reaching consequences, user privacy, data integrity, and even physical safety.












