In today’s interconnected landscape, safeguarding external accessible interfaces demands a security-first mindset. Ensuring the protection of sensitive data and the reliability of systems relies on adhering to key secure design principles. In an age dominated by digital interconnectivity, the creation of external accessible interfaces is not merely a functional task-it is a responsibility to safeguard sensitive data and uphold the trust of users.
Security must be ingrained in the very fabric of these interfaces, ensuring not only seamless functionality but also the confidentiality, integrity, and availability of the data they handle. In this exploration of secure design principles, we delve into key strategies that provide a robust defense against potential threats, creating a foundation upon which secure external interfaces can thrive.
WHAT IS SECURE BY DESIGN?
“Secure by design” is a principle in cybersecurity and software development that emphasizes incorporating security measures and considerations into the design of systems, applications, or processes from the initial stages. This proactive approach aims to identify and address potential security risks and vulnerabilities during the design phase, creating more resilient and secure solutions.
By integrating security considerations into the design process, organizations can reduce the likelihood of security breaches, minimize the attack surface, and establish a robust defense against potential cyber threats. This approach involves implementing secure default settings, adopting least privilege access controls, considering fail-secure designs, and prioritizing explicit allowlists over denylists. Overall, “secure by design” promotes a proactive and strategic mindset towards cybersecurity, fostering resilient systems that can withstand emerging challenges.
SECURE BY DESIGN PRINCIPLES
1. External or Internal Accessibility
This section delineates whether the interface is externally accessible, internally accessible, or both, providing clarity on the interface’s reach within the product architecture.
2. Product Security Context and External Interface
Discuss the impact of the product’s security context on the external interface, emphasizing how the product’s security measures influence and interact with external accessibility.
3. Interface Users and Accessible Assets
Identify potential users of the interface and the assets accessible through it, elucidating both direct and indirect access scenarios.
4.Crossing Trust Boundaries
Determine if access to the interface involves crossing trust boundaries within the product’s ecosystem, highlighting any security implications associated with boundary traversal.
5. Interface Security Landscape
Outline security considerations, assumptions, and constraints associated with interface usage within the product security context, including a thorough examination of applicable threats.
6. Security Roles and Access Control
Define security roles, privileges, and access control permissions required to use the interface, emphasizing the protection of assets identified.
7. Security Safeguards for the Interface
Detailed security capabilities and compensating mechanisms employed to protect the interface and associated assets. Include robust input validation, output handling, and error management strategies.
8. Third-Party Products and Security Capabilities
Assess the use of third-party products in implementing the interface, providing insights into their security capabilities, and ensuring alignment with the overall security objectives.
9. User Documentation for External Accessibility
Offer comprehensive documentation for users accessing the interface externally, facilitating a secure and efficient understanding of its functionalities.
10. Threat Mitigation in Interface Design
Provide a detailed description of how the interface design mitigates identified threats from the threat model, offering a proactive approach to security challenges.
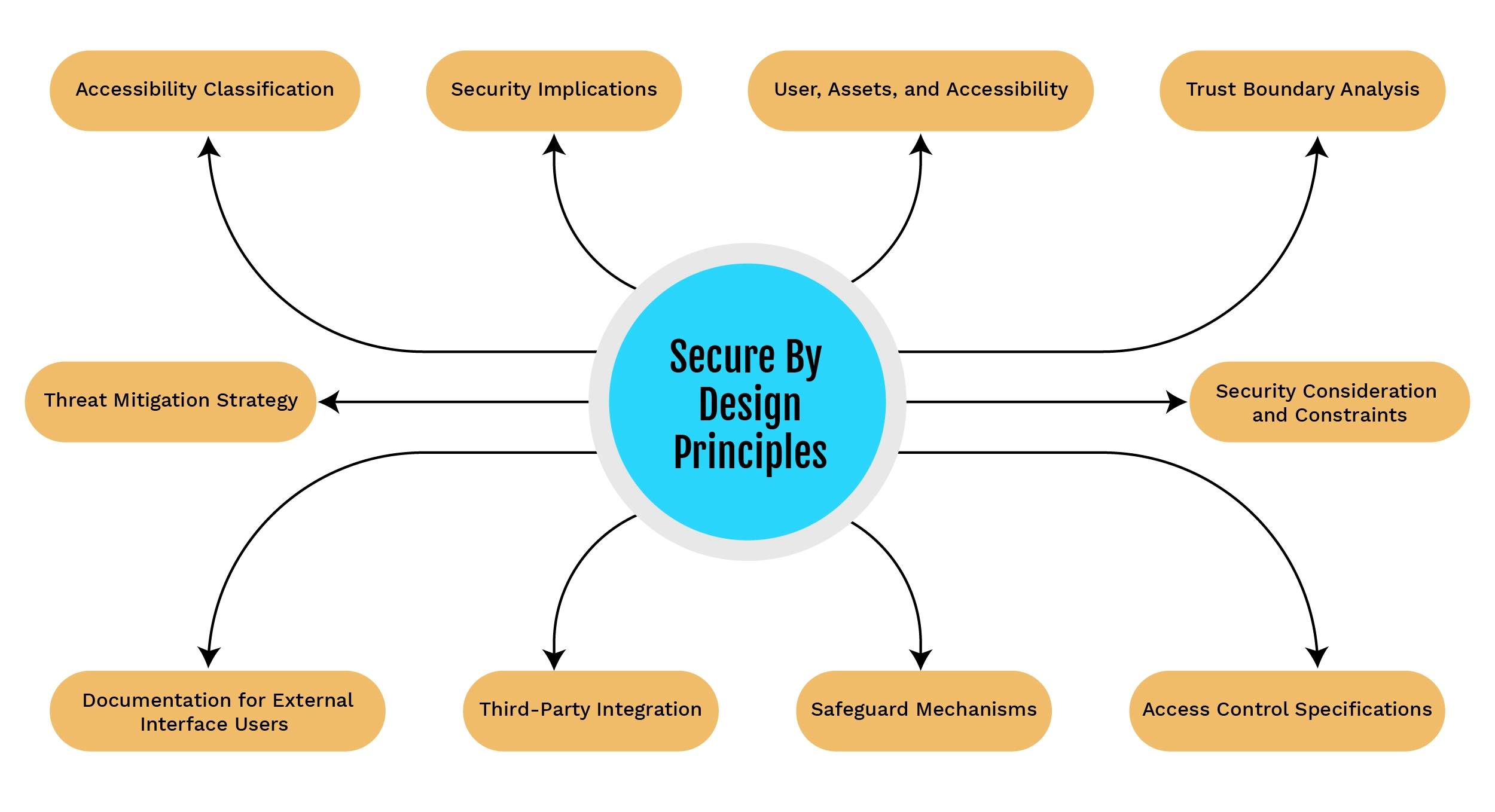
Figure: Secure By Design Principles
Key principles include deploying multiple layers of security controls, not dismissing mitigations even if they don’t fully resolve an issue, if some defenses will fail, and balancing defense with factors like complexity and cost. The emphasis is on a proactive mindset, preparing for potential failures, and implementing cost-effective measures based on the value of assets. An example highlights the importance of addressing specific threat model findings, such as encrypting traffic to a Relational Database Service (RDS). This comprehensive strategy aims to create a resilient and adaptive security posture by avoiding single points of failure and anticipating the dynamic nature of cyber threats.
Adopt secure default settings, implement least privilege access controls, design services to fail securely, and prioritize allowlists over denylists for explicit authorization. Implement a least privileged model, denying access by default and enabling only necessary services, threats, or accounts to reduce the attack surface. Set secure configurations as default, reducing reliance on user adjustments, and minimizing the risk of misconfigurations.
SECURING INCLUSIVE INTERFACES: THREAT MITIGATION & THIRD-PARTY SECURITY
1. Accessibility:
Consideration: Ensure the product is accessible to all users, including those with disabilities, by following accessibility standards such as WCAG (Web Content Accessibility Guidelines).
Implementation: Incorporate features like screen reader compatibility, keyboard navigation, and alternative text for images to enhance usability for individuals with diverse needs.
2. Safeguarding Measures:
Consideration: Implement protective measures to mitigate security risks and vulnerabilities.
Implementation: Integrate robust authentication mechanisms, encryption protocols, access controls, and regular security audits to safeguard against potential threats and unauthorized access.
3. Use of Third-Party Products for the Interface and Their Security Capabilities:
Consideration: Evaluate and manage the security implications of third-party products or components integrated into the interface.
Implementation: Regularly assess the security posture of third-party products, ensure they adhere to security best practices, and stay informed about updates or patches. Implement secure APIs and communication protocols for seamless integration.
4. Mitigation of Threats Identified in the Threat Model:
Consideration: Address and mitigate potential threats identified through a comprehensive threat modeling process.
Implementation: Integrate security controls and countermeasures into the design to specifically address identified threats. This may include implementing encryption for data in transit, input validation to prevent injection attacks, and secure error handling to avoid information disclosure.
5. Product’s Security Context Affecting the External Interface:
Consideration: Understand how the overall security context of the product influences its external interfaces.
Implementation: Implement security measures at the interface level based on the product’s security context. This may involve incorporating secure communication protocols, enforcing access controls, and considering the impact of external dependencies on overall system security.
In conclusion, “Secure by design” is a fundamental and proactive approach to cybersecurity that underscores the importance of building resilient systems from the outset. By integrating security measures into the design process, organizations can mitigate risks, reduce vulnerabilities, and create a robust defense against evolving threats. This principal advocates for secure default settings, least privilege access controls, fail-secure designs, and explicit allowlists. Embracing “secure by design” not only enhances the overall security posture of systems but also instills a proactive mindset that is crucial in today’s dynamic and challenging cybersecurity landscape.
From Einfochips
IoT equipment is required for all types of businesses. Businesses must implement strong safety protocols for their IoT devices to protect their assets, data, and infrastructure from potential threats. By implementing these processes, organizations can mitigate the impact of an incident and reduce the risk of successful assaults.
eInfochips has proven invaluable in assisting organizations handle security products on a global scale. We are specialists in securing connected device networks across all network layers, including device connection and apps. Because of our strategic, transformative, and managed operations philosophies, we can provide comprehensive cybersecurity services. This includes not just vulnerability assessment and penetration testing (VAPT) for OT/IoT devices, operating systems/firmware, web/mobile applications, data, and infrastructure, but also threat modelling.












