Introduction
In the rapidly evolving landscape of web application development, security is paramount. As organizations and individuals rely more heavily on web-based services, ensuring the confidentiality, integrity, and availability of sensitive data is crucial. Authentication mechanisms play a pivotal role in this endeavor, and Microsoft’s Azure Active Directory (Azure AD) provides a robust framework to achieve this.
This introduction delves into the world of .NET web application authentication, where we explore the use of Azure Active Directory (Azure AD) in conjunction with Microsoft Authentication Library (MSAL) and Proof Key for Code Exchange (PKCE) implementations. These technologies form a powerful arsenal for building secure and user-friendly web applications.
Problem Statement
The organization needs to enhance the security and user authentication process for our .NET web application. We want to migrate from traditional username/password-based authentication to a more secure and modern authentication method using Azure Active Directory (Azure AD). We aim to implement the Microsoft Authentication Library (MSAL) and Proof Key for Code Exchange (PKCE) in our web application to achieve this.
What is Azure Active Directory (Azure AD)?
Azure AD is a cloud-based identity and access management service that helps manage your employees’ access to external resources, like Microsoft 365 and the Azure portal, as well as thousands of other software-as-a-service (SaaS) applications. It also gives them access to internal resources, like apps on your company’s intranet and any cloud apps created specifically for your business.
What is Microsoft Authentication Library (MSAL)?
Developers can obtain security tokens from the Microsoft Identity Platform to authenticate users and access secure web APIs through the Microsoft Authentication Library (MSAL). This provides fast access to Microsoft Graph, other Microsoft APIs, third-party web APIs, or your web APIs. MSAL is compatible with many application platforms and architectures, including .NET, JavaScript, Java, Python, Android, and iOS.
Benefits of MSAL
- Obtain a token on a user’s or application’s behalf (if applicable to your platform).
- Maintains a token cache and refreshes tokens as they near expiration.
- You don’t have to worry about expiring tokens yourself.
- Helps you specify which users your application will log in to. Sign-in audiences can include the social identities of individuals’ Microsoft accounts, Azure AD B2C organizations, businesses, schools, and state and national cloud users.
- Helps you set up your application using configuration files.
- Helps you troubleshoot your apps by uncovering actionable exceptions, logs, and telemetry.
- You don’t need to use an OAuth library or the protocol code directly in your application.
What is proof key for code exchange (PKCE)?
In a world where security threats are continually evolving, it’s crucial to protect your applications against various attacks. PKCE, pronounced “pixy,” adds an extra layer of security to the authentication process by safeguarding the exchange of authorization codes. This method is critical when dealing with single-page applications (SPAs) and mobile apps. PKCE is the Proof Key for Code Exchange started with OAuth 2.0 Authorization Code Grant.
Flow Diagram:
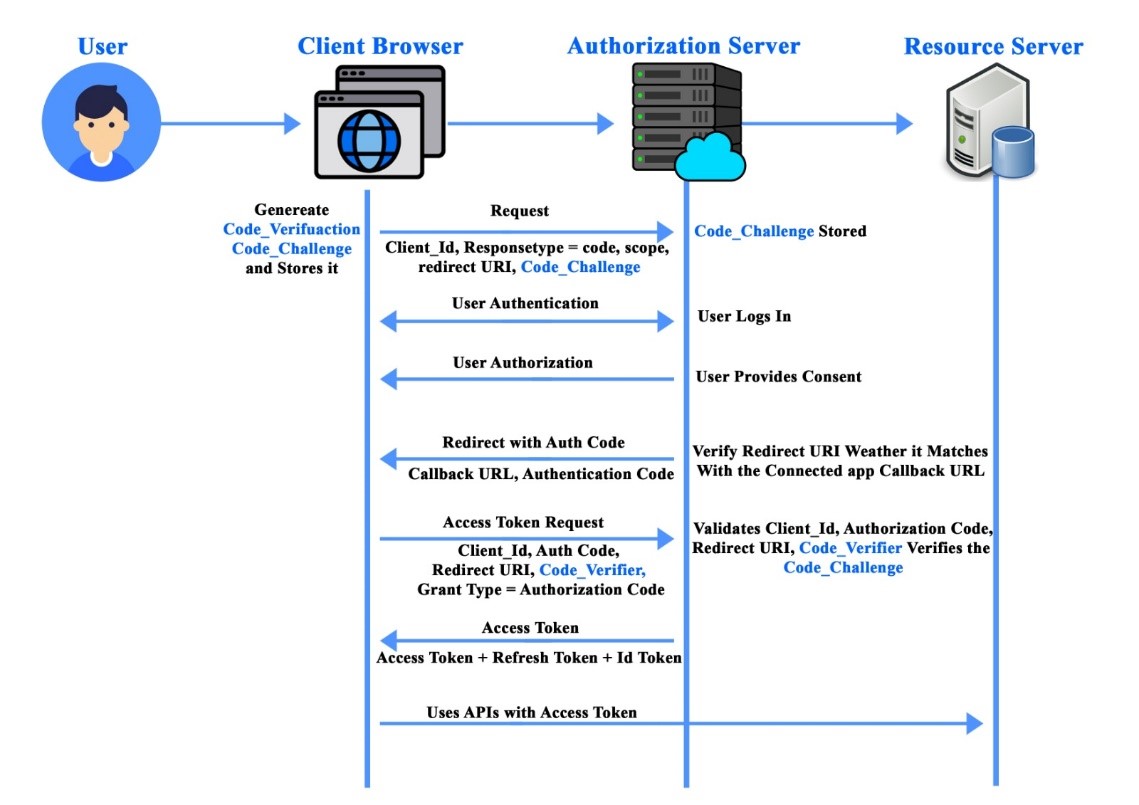
PKCE Flow
- The first user requests the resource via a client browser.
- Code verifiers and code challenges are generated and stored on the client side.
- The request is sent to the authorization server along with the client_id, response type, redirect URI, code challenge, and challenge method used to generate the code challenge.
- Code challenges and methods are stored on the authorization server.
- The user is then authenticated and authorized.
- Redirect the user using the authentication server callback URI and authentication code.
- The access token that includes the previously generated client_id, scope, redirect URI, grant type, and code reviewer is then requested from the user.
- The Authorization Server verifies the facts dispatched with the aid of using customer and confirms the code verifier with code venture in advance dispatched.
- If validation is successful, an access token, refresh token, and client token are sent to the client.
- Using the access token, the client requests data from the resource server.
Create .NET web application with MSAL and PKCE calling Microsoft Graph API for fetching usernames.
- Create a new ASP.NET Core Web Application (Model-View-Controller) and click the Next button.
2. Name your application, choose a location to save it, and click the Next button.
3. Select .Net Core version at least .Net Core 5 or higher and click the Create button.
4. Install the subsequent NuGet Packages.
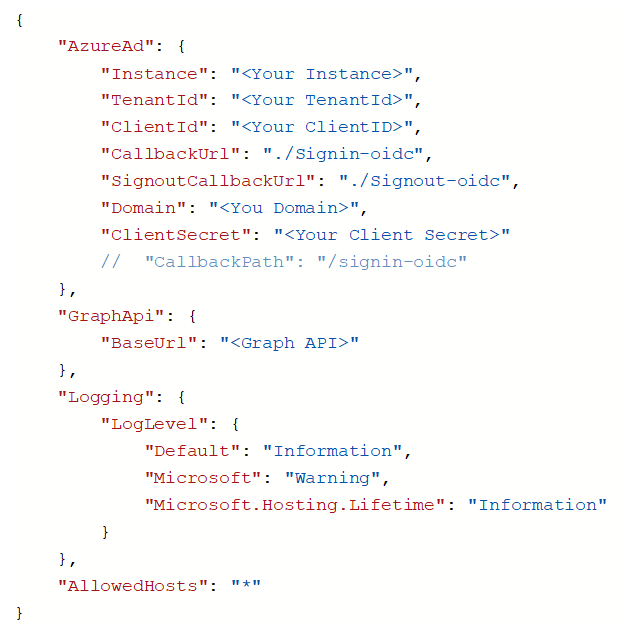
5. Next, open the appsetting.json file and add the following code. Azure AD configuration is obtained from the Active Directory created in the Microsoft portal.
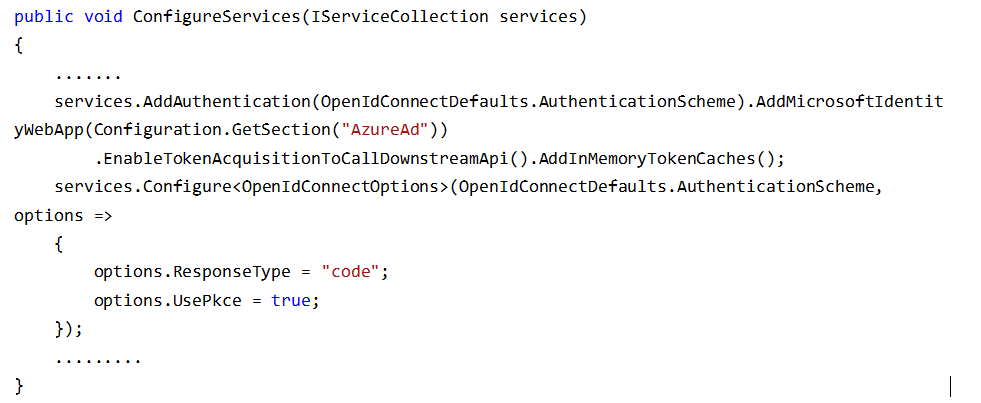
6. Open the startup file and add the following code to “Configure Service”.
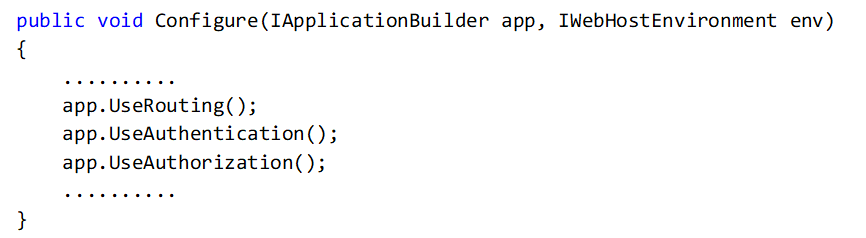
7. Under Configure, add authentication and authorization for the following usage:
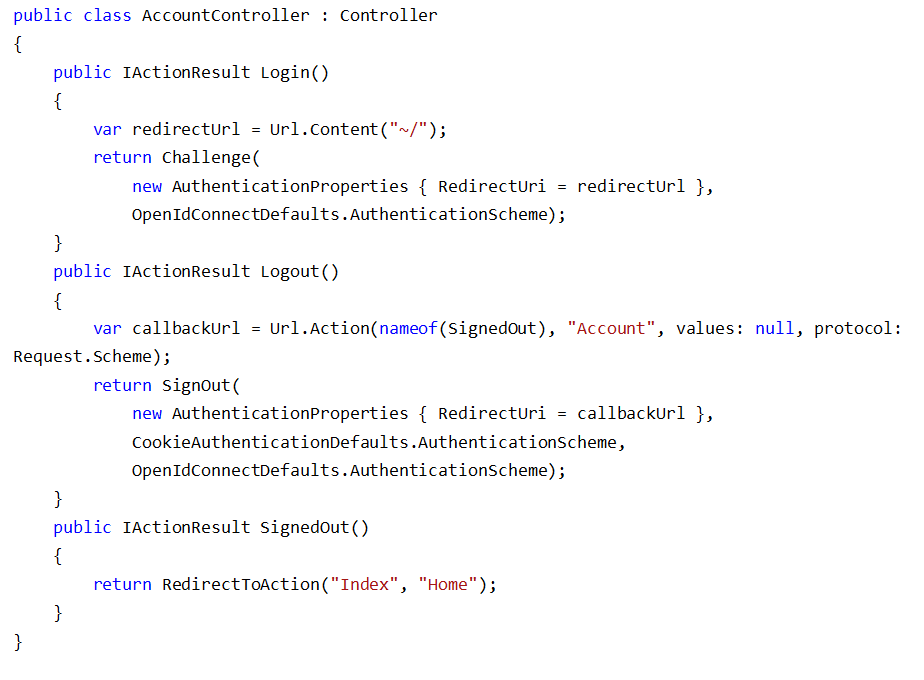
8. Create a controller account controller for the login and logout action methods.
9. Create a graph controller to help you retrieve data for your users.
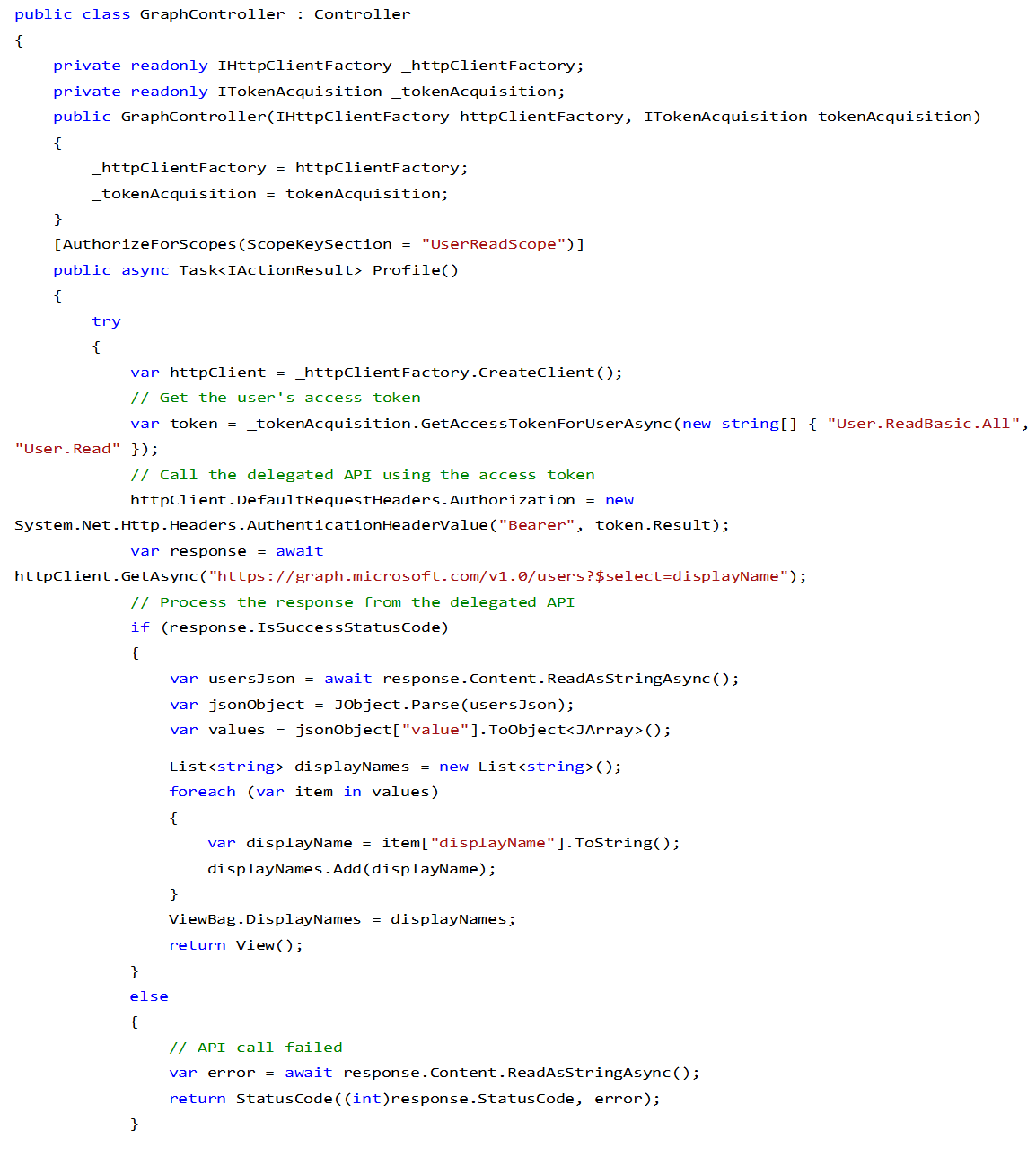
Here the token can be taken from the cookies and can be dispatched with the Graph API header for the authentication.
10. Edit the header part of the layout page as follows.
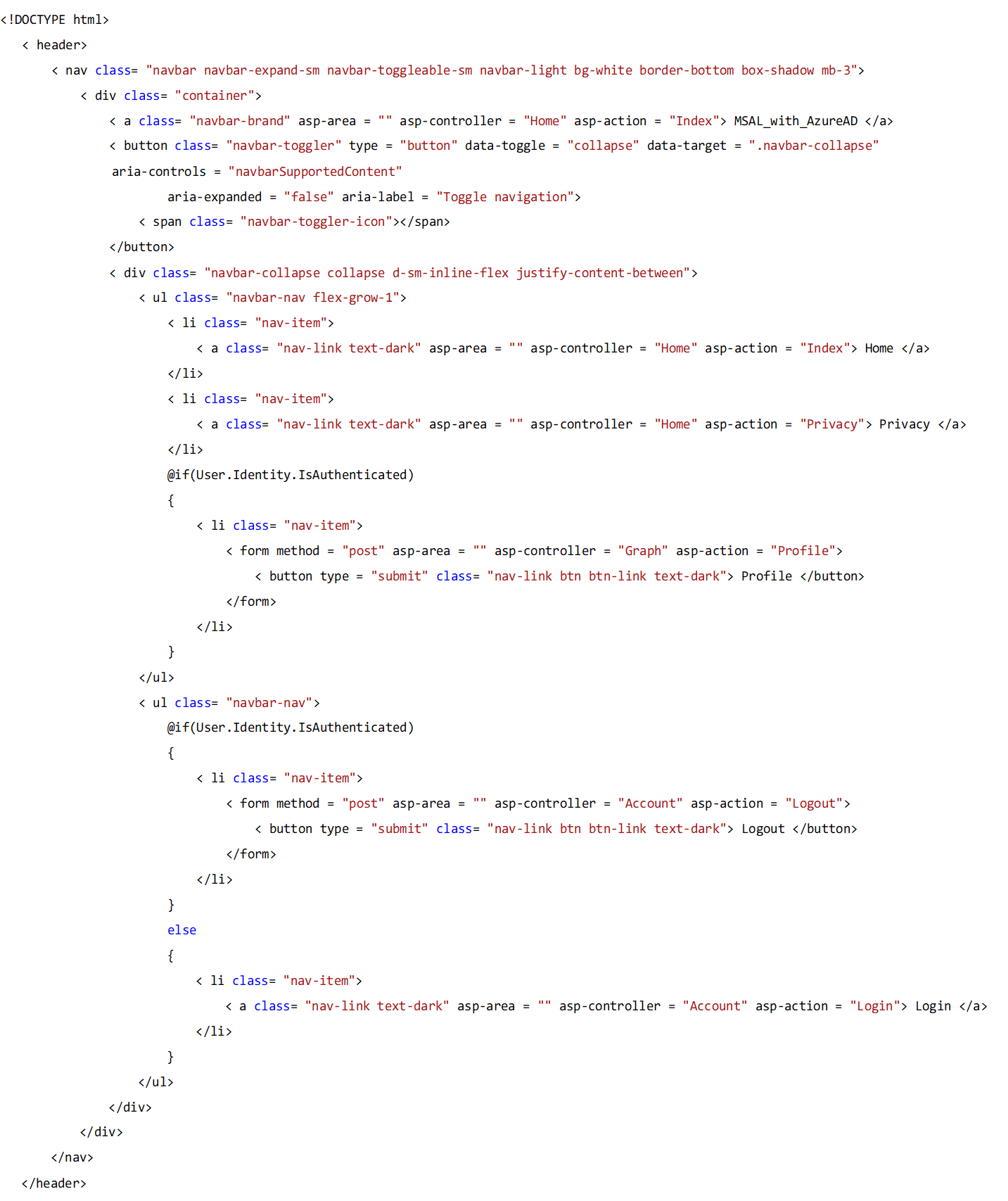
11. Create a new view page index in the diagram folder inside the views folder. Once the token is validated, the API returns data to a JSON file. It will be displayed on the browsing page.
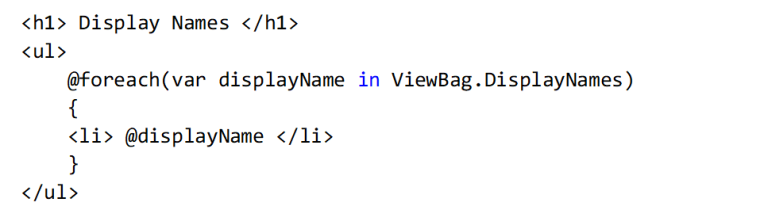
12. Finally, we get the results from the API.
Conclusion
In conclusion, implementing authentication in a .NET web application using Azure Active Directory, MSAL (Microsoft Authentication Library), and PKCE (Proof Key for Code Exchange) represents a significant step forward in enhancing security, user experience, and overall application reliability. Implementing .NET web application authentication with Azure Active Directory, MSAL, and PKCE offers a powerful solution for securing your application, ensuring a smooth user experience, and simplifying development. By utilizing these technologies, you can confidently protect user identities, manage access, and maintain the integrity and reliability of your application, all while delivering a seamless and user-friendly experience. This authentication framework serves as a foundation for building trust with your users and stakeholders, ensuring the long-term success of your web application.
References
https://datatracker.ietf.org/doc/html/rfc6749#section-4.1
https://learn.microsoft.com/en-us/entra/identity-platform/msal-overview
https://learn.microsoft.com/en-us/answers/questions/218113/openid-connect-authorization-code-flow-with-proof












