Malicious software is meant to harm your network or computer system. Malware differs from conventional programs; it can travel over a network unnoticed, modify or harm and infect systems or network, and survive. They can completely damage a network and significantly degrade machine performance.
What is Malware?
Malware, short for “malicious software,” refers to any software or code that is designed to harm, exploit, or disrupt computer systems, networks, or devices without the consent of the user. It is a broad term that encompasses various types of malicious software, including viruses, worms, Trojans, ransomware, spyware, adware, and more.
The intentions behind malware can vary. Some malware is designed to steal sensitive information, such as login credentials, financial data, or personal information, while others may aim to disrupt computer systems or networks, causing damage or inconvenience. Malware can be distributed through various means, including malicious email attachments, infected websites, software vulnerabilities, or through the exploitation of user behavior, such as social engineering techniques.
Malware can have severe consequences, including data breaches, financial loss, identity theft, system crashes, and compromised privacy. To protect against malware, it is important to use security measures such as antivirus software, firewalls, regular software updates, and safe browsing practices. Additionally, being cautious while opening email attachments, downloading software from trusted sources, and avoiding suspicious websites can help reduce the risk of malware infections.
What is Machine Learning?
Organizations worldwide are scrambling to incorporate machine learning into their operations, as a result, opportunities for aspiring data scientists are multiplying. One of the most intriguing capabilities of machine learning techniques is the – Ransomware detection using machine learning algorithms like SVM, Logistic, Regression, Trees, Random Forest.
Algorithms are taught using statistical techniques to produce classifications or predictions and to find important insights in data mining projects. As the name suggests, it gives modern devices the power to analyze data and learn, which empowers them with the human-like ability to analyze, understand and perform complex tasks.
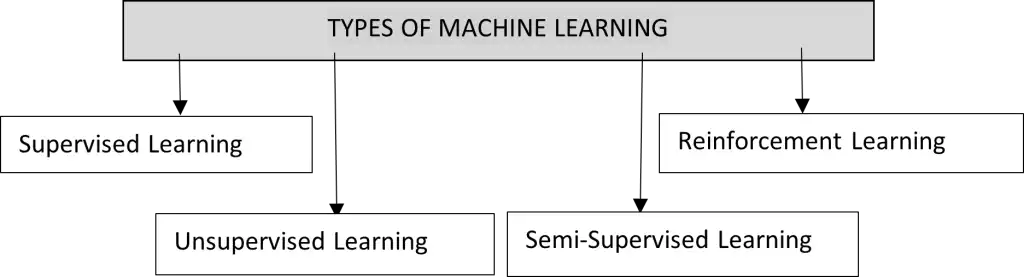
Types of Machine Leaning
Supervised Learning
This technique uses “labelled” datasets to train algorithms to predict output based on the training. Labeled data indicates that some of the inputs have already been mapped to the output in this case. Supervised learning can be categorized into two types of methods – classification and regression. After training the machine with input and output, it uses the test dataset to see if the machine can predict the output.
Unsupervised Learning
Unsupervised learning involves training models on data that has not been classified or labeled allowing the model to act on its data without supervision. When conducting exploratory data analysis, unsupervised learning is frequently used to identify characteristics and create classes based on groupings. Machines are instructed to seek out hidden patterns within the input dataset. Common unsupervised data learning approaches are clustering, dimensionality reduction and association rules algorithms.
Semi-Supervised Learning
In machine learning, the intermediate ground is called semi-supervised learning. It deals with some labelled data and a lot of unlabeled data; supervised learning is required to help algorithms identify unlabeled data. Semi-supervised algorithms, however, can let you train your model without labelling every training case, thus saving a lot of time and money. One of the classic Semi-Supervised learning use cases is text document classifier. With a small amount of labeled data, algorithms can learn to classify large amounts of unlabeled data. Self-training is one of the semi-supervised learning techniques that leverage supervised learning methods to make the most of the mixed data sets containing labeled and unlabeled data.
Reinforcement Learning
Decision science is known as reinforcement learning, or RL. To get the most out of an environment, one should train itself to exhibit the best conduct. Different from supervised learning model, in reinforcement learning, the model is trained without any training data sets with the answer key, thus, the model does not know the correct answer and must depend on the reinforcement agent to perform a given task in the most optimal manner by learning from experience. Some of the examples where Reinforcement learning technique is used are Video games, Robotics and Text mining.
Malware Detection Using Machine Learning Techniques
All malware detection methods can be classified as signature-based or behavior-based. It is essential to comprehend the principles of the two malware analysis methodologies, static analysis, and dynamic analysis, before diving into these techniques.
Static analysis, as the name implies, is performed ‘’statically,’ that is, without running the file while dynamic analysis is done by executing the file on a virtual machine. Static analysis can be thought of as “reading” the malware’s source code to deduce the file’s behavioral properties. Various techniques used in the static analysis:
- File Format Inspection Metadata in files can be particularly useful. For instance, PE (portable executable) files may offer a plethora of data regarding build time, functions that are imported and exported, and more.
- String Extraction is the process of scrutinizing software output (e.g., status or error messages) and extracting information about malware operation.
- Fingerprinting entails performing cryptographic hash computations and locating environmental artifacts such as hardcoded usernames, filenames, and registry strings.
- AV inspection scanners will identify any well-known malware in the examined file. Although it might seem trivial, antivirus and sandboxes commonly employ this kind of detection to “confirm” their findings.
- Disassembly involves translating machine code into assembly language to deduce the logic and intents of the software. The most popular and reliable approach of static analysis is this one.
Dynamic analysis is yet another type of analysis. The behavior of the file is observed during execution, as opposed to static analysis, and the attributes and intents of the file are deduced from that data.
Normally, the file is executed in a virtual setting, like a sandbox. This kind of analysis allows for the discovery of all behavioral characteristics, including opened files, produced mutexes, and other things. It is also comparatively faster than static analysis.
The procedure of training the machine learning model to predict the output is described below through an example of a Training Phase.
Training Phase of the Algorithms
Solving the malware detection problem by leveraging machine learning techniques follows a particular pipeline, as shown in the above figure. The benign and malware binaries to be used for training ML model are collected for the training process. A feature extractor processes these binary files to extract information about them (such as file size and section information), which is then fed to the machine learning model.
How Machine Learning Works in Malware Detection in Antiviruses
To understand the process let’s take the example of Microsoft defender’s team to learn How they combat a spate of Java malware using malware techniques .
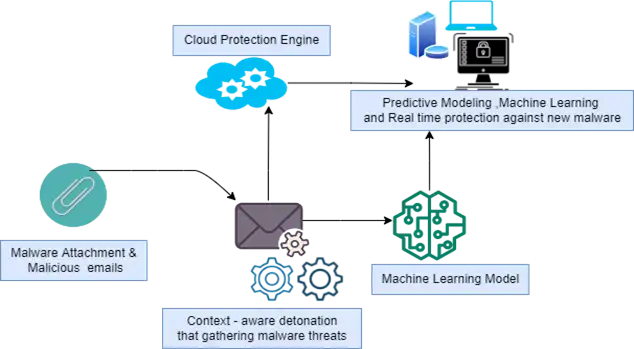
“Machine Learning has improved the ability to offer defense against the most recent, never-before-seen malware. These expert systems provide real-time visibility and context into attacks, allowing Windows Defender AV to provide real-time protection against a wide range of threats.
Context-aware detonation systems collect massive amounts of threat intelligence by analyzing millions of potential malware samples. Cloud security engines receive this threat knowledge as input, enabling real-time attack detection and prevention. In addition to Java malware, windows defender also searches for the payloads, which are typically Java remote access Trojans (RATs) such as Jrat and Qrat or online banking Trojans (such as Banker and Banload).”
Organizations must continually monitor and correlate millions of internal and external data elements from their user base and infrastructure to stay safe from cyber-attacks. However, it’s easier said than done since it’s impossible to monitor and process such a huge amount of information manually. In situations like these, machine learning excels, because it can swiftly identify trends and foresee dangers in various types of data sets. Cyber teams may identify risks more rapidly and separate circumstances that call for more in-depth human study by automating the analytic process.
Einfochips provides all-round cyber security services for threat modelling, VAPT (Vulnerable Assessment Penetration Testing) devices, OS/firmware, web/mobile applications, data, and cloud workloads to detect and classify malware using Machine Learning techniques like Signature-based algorithm, Feature Extraction, Static Analysis and Dynamic Analysis etc.
Moreover, many tools like Virustotal, Process monitor, Regshot, Wireshark, Procmon, etc. are used to classify malware types like trojans, backdoors, types of viruses and worms, Rootkits etc. This approach ultimately assists customers in deploying secure products in the open world, which helps protect products from Malicious Software.
By strategic, transformative, and managed operations techniques eInfochips has assisted businesses in the development, deployment, and management of security solutions on a worldwide scale to satisfy security industry standards, rules, and guidelines like NIST (National Institute of Standards and Technology), ENISA (European Netword and Information Security Agency), OWASP (Open Web Application Security Project), MITRE (Massachusetts Institute of Technology Research and Engineering), and IoT Security Foundation.