Secure Boot protects devices from boot-time threats by ensuring that only trustworthy software is loaded during the boot process. It works by verifying the digital signature of each piece of firmware and software loaded during boot, to make sure it hasn’t been tampered with or altered by malicious actors. Secure Boot is implemented in the firmware of a device, such as the BIOS or UEFI (Unified Extensible Firmware Interface), and it checks the digital signature of the bootloader, operating system kernel, and other firmware components before allowing them to execute. If the digital signature is not valid, Secure Boot prevents the software from executing and alerts the user or administrator.
Secure Boot helps protect against a wide range of attacks, including rootkits, boot kits, and firmware-level malware, which are difficult to detect and remove once installed. It is a widely adopted security feature and is supported by many operating systems, including Windows, Linux, Android, and iOS. It is also commonly used in devices such as laptops, desktops, servers, and embedded systems. We use Secure Boot to enhance the security of devices and systems and protect them against boot-time attacks.
Why do we need secure boot in IoT devices?
Secure boot is an essential security feature in IoT devices that helps ensure the integrity and authenticity of the device’s software and firmware. Here are several reasons why secure boot is crucial for IoT devices:
Preventing unauthorized software: Secure boot helps prevent the execution of unauthorized or malicious software on IoT devices. It verifies the integrity and authenticity of software during boot, ensuring only properly signed and trusted software is loaded.
Protecting against firmware tampering: IoT devices often have firmware that controls their operation. Secure boot ensures that the firmware hasn’t been tampered with or modified by unauthorized individuals. It detects any unauthorized changes, such as the insertion of malware or malicious code, and prevents the device from booting if such changes are detected.
Counteracting supply chain attacks: Secure boot mitigates the risk of supply chain attacks, where attackers attempt to compromise devices during the manufacturing or distribution process. By verifying the authenticity and integrity of the software and firmware at boot time, secure boot helps ensure that only trusted components are present in the device.
Enhancing overall system security: Secure boot is a foundational security measure that strengthens the overall security posture of IoT devices. It provides a trusted starting point for the device’s operation and helps establish a chain of trust for subsequent software and firmware updates. By ensuring that only authorized and properly signed code runs on the device, it reduces the attack surface and improves resistance to various security threats.
Secure boot process in IoT devices
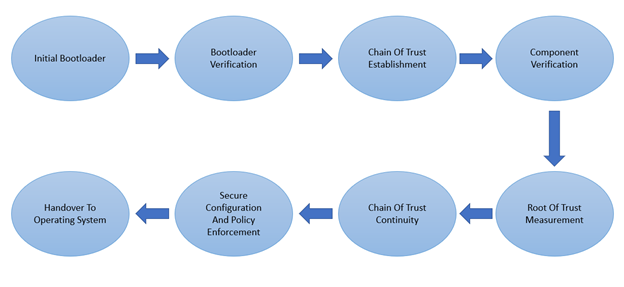
Initial Bootloader: The process starts with the device’s Boot ROM or an initial bootloader. This component is typically stored in read-only memory and is responsible for initializing the device and loading the next stage of the boot process.
Bootloader Verification: The initial bootloader verifies the integrity and authenticity of the subsequent bootloader stage. It checks the digital signature or hash of the bootloader using cryptographic algorithms and compares it against the trusted signature or hash stored in secure memory.
Chain of Trust Establishment: If the verification of the bootloader is successful, it establishes a chain of trust by securely loading and executing the next stage in the boot process. This stage can be another bootloader, a secure monitor, or a trusted execution environment (TEE).
Component Verification: Each subsequent component in the boot process, such as the secure monitor or TEE, is verified for integrity and authenticity. This involves validating digital signatures or hashes to ensure that the components haven’t been tampered with or modified.
Root of Trust Measurement: As each verified component is loaded, the device measures its integrity by calculating a hash or cryptographic measurement of the component. This measurement is stored securely in a dedicated hardware or software-based root of trust, establishing a record of the component’s integrity.
Chain of Trust Continuity: The secure boot process continues with subsequent components, such as the operating system kernel, device drivers, and critical software libraries. Each component is verified, measured, and securely loaded based on the established chain of trust.
Secure Configuration and Policy Enforcement: The secure boot process enforces secure configuration settings and policies defined by the manufacturer or system administrator. This can include restrictions on running unsigned code, enforcing specific security requirements, or validating software against a whitelist of trusted applications.
Handover to Operating System: Once all verified components have been loaded, the secure boot process hands over control to the operating system. At this stage, the operating system can trust that the boot process has been protected from unauthorized or malicious software, and it can start executing its tasks with a higher level of confidence.
The above steps provide a generalized overview, and actual implementations may include additional security measures or variations based on the specific IoT device and its architecture. The overall goal is to establish a secure foundation for the device’s boot process, ensuring the integrity and authenticity of software components and protecting against unauthorized or malicious code execution.
Secure Boot is a key security feature, Secure Boot can assist in improving the security of Internet of Things (IoT) devices. In IoT security Secure Boot protects against firmware-level attacks. secure Boot verifies the digital signature of the firmware and software that is loaded during boot, which helps prevent firmware-level attacks such as rootkits and boot kits. These types of attacks are difficult to detect and can compromise the security of the device and the data stored on it.
Secure Boot ensures that only trustworthy software is executed by checking the digital signature of each piece of software that is loaded during boot. This helps prevent malware and other unauthorized software from being loaded and executed on the device. prevent unauthorized modifications. secure Boot prevents unauthorized modifications to the bootloader, operating system, and other firmware components, which helps ensure the integrity of the system and prevent tampering. support for industry standards. Secure Boot is now a widely adopted security feature and is supported by many operating systems and devices. By using Secure Boot, devices and systems can be designed to comply with industry standards and best practices for security.
In simple terms, Secure Boot in IoT devices is a security feature that ensures only trusted software can run during the device’s startup. It uses special keys to check the digital signatures of critical components like the operating system and device drivers. If the signatures are valid, it means the software is authentic and secure, allowing the device to proceed with the startup process. This helps protect against malicious software and enhances the overall security of the IoT device.
Benefits of Secure boot in IoT devices
Firstly, it protects against unauthorized code execution by ensuring that only trusted and properly signed software components are executed during the boot process. This prevents the device from running unauthorized or malicious code, thereby safeguarding against potential security threats. Secondly, secure boot enhances system integrity by verifying the integrity of software components, ensuring that the device’s firmware and critical software haven’t been tampered with or modified. This strengthens the overall system integrity and reduces the risk of compromised or unreliable operations. Furthermore, secure boot mitigates supply chain risks by verifying the authenticity of software components during the boot process, protecting against tampering or substitution of software during manufacturing, distribution, or deployment. This ensures that the device operates with genuine and trusted software. Additionally, secure boot helps reduce malware infections by acting as a defense mechanism, preventing the execution of unauthorized or malicious code. It helps mitigate the risk of malware and protects the device and its data from potential compromise or damage.
Secure boot also ensures the trustworthiness of firmware and software by establishing a chain of trust, validating each component in the boot process. This ensures that the firmware, operating system, and critical software are from trusted sources and haven’t been tampered with, enhancing the overall trustworthiness of the device. Moreover, secure boot supports compliance with security standards and regulations specific to IoT devices, providing evidence of a secure boot process and demonstrating adherence to security requirements. It enables secure over-the-air (OTA) updates by verifying the integrity and authenticity of updated software components, ensuring that only authorized and properly signed updates are installed on the device, reducing the risk of compromised updates.
Finally, secure boot enhances the resilience of IoT devices by protecting against unauthorized code execution and tampering. It helps maintain device availability, prevents disruptions caused by malware or compromised software, and ensures reliable operation in various IoT applications. Overall, implementing secure boot in IoT devices is crucial for protecting against security threats, ensuring system integrity, mitigating supply chain risks, and enhancing the trustworthiness and resilience of the devices.
How to Enhance IoT Security with Secure boot
At eInfochips, we have an IoT security team. Here we are committed to helping businesses enhance the security of their IoT devices with secure boot. Our expert IoT security team is equipped with extensive knowledge and experience to deliver comprehensive services that protect your devices from unauthorized access and tampering. We offer a range of services that include detailed guidance and support throughout the consulting process, where we provide guidance on secure boot implementation strategies, conduct threat modeling, and risk assessments, and advise on cryptographic algorithms and key management practices that align with industry standards. Additionally, we assist in customizing the Secure Boot process based on the specific requirements and constraints of the IoT devices.
Furthermore, we conduct comprehensive security assessments and penetration testing of IoT devices to identify vulnerabilities and weaknesses in Secure Boot implementations. Through these assessments, we help our clients uncover potential attack vectors, ensure proper configuration, and validate the effectiveness of Secure Boot mechanisms. We also offer code reviews and firmware analysis services to identify any potential security risks.
Overall, we provide valuable support in implementing and managing Secure Boot for IoT devices, helping organizations navigate the complexities of IoT security, address vulnerabilities, and establish a robust security posture for their IoT deployments. By leveraging our expertise, we ensure enhanced security and protection against boot-time attacks.
By partnering with eInfochips, IoT device manufacturers and developers can benefit from our expertise in securing devices through effective secure boot implementations. We work closely with clients to strengthen device security, protect against unauthorized code execution, and mitigate risks associated with supply chain tampering and malware infections.
Conclusion
Secure Boot is a crucial security feature that enhances the protection of IoT devices by verifying the authenticity and integrity of firmware and software components during the boot process. By ensuring that only trusted software is executed, Secure Boot guards against boot-time attacks and prevents unauthorized modifications. It requires expertise in cryptographic algorithms, key management, and customization based on device requirements. Comprehensive security assessments, code reviews, and compliance adherence further strengthen the implementation. Embracing Secure Boot enhances the security and integrity of IoT devices, safeguarding them in the evolving landscape of connected devices.












