Introduction to the automotive industry and its challenges
The automotive industry is huge and comprises organizations involved in the design, innovation, development, manufacturing, marketing, and selling of connected vehicles. If we consider the revenue, it is one of the largest industries in the world.
In modern connected vehicles, there are more than 100 microprocessors (Micro Controller Units – MCUs), 40 plus Electronic Control Units (ECUs), and thousands of lines of software codes. The automated vehicles can connect via Bluetooth, built-in cellular communication, and Wi-Fi for various applications.
Vehicle connections can be Vehicle to Infrastructure(V2I), Vehicle to Vehicle, Vehicle to Cloud, and Vehicle to Everything (V2X). Any vulnerabilities left within the system can open doors for hackers to manipulate it.
Due to evolution in the industry, we must address automotive challenges such as safety, security, reliability, cost, durability, and use of modern embedded controllers. Some of the existing security standards do not address these automotive challenges.
The ISO 21434 standard, exclusively designed for road vehicles helps address all these issues and ensures appropriate cybersecurity. It provides objectives, requirements, and guidelines as a foundation for common understanding throughout the supply chain. It also defines how organizations should be well-prepared to mitigate the organizational level risks and the security risks in the vehicles.
The ISO 21434 standard creates a standardized set of evaluation criteria so that Original Equipment Manufacturers (OEMs) and suppliers can confidently sign off on hardware and software configurations knowing that the desired degree of cyber security evaluation standards has been met. Below is a snippet from ISO 21434 that depicts the flow of the threat analysis and risk assessment method.
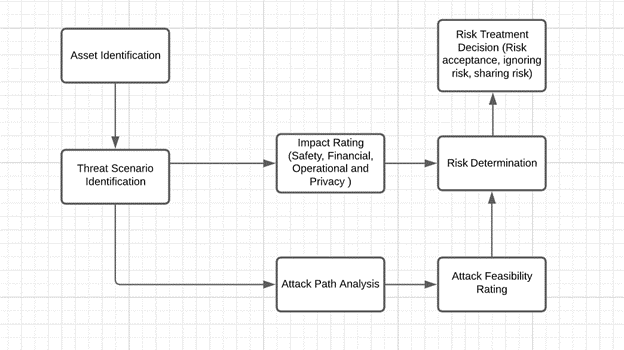
One cannot assure the safety of a vehicle if its security is not up to the mark as there is no safety without security. It is a must to implement proper security measures in all the layers of the electronics to protect critical features and back-end networks that may become a breeding ground for cyberattacks. To achieve this, the OEMs and suppliers should get themselves certified with the ISO 21434 automotive security standard.
Automobile safety is the study and practice of design, construction, equipment, and regulation to minimize the occurrence and consequences of threats and mishaps. It is evaluated and measured against the ISO 26262 standard, which defines the functional safety standards for the development and production of automotive products.
It is an approach to make electronic components inside a car reliable and safe. It contains policies, guidelines, and regulations to minimize the impact on drivers, passengers, and pedestrians from the occurrence and consequences of collisions and faults in electronics and software.
Attack surface, attack vectors, and cyberattacks on automotive vehicles
Now since we have built a foundation in the automotive industry, let’s shift our focus to attack surfaces, attack vectors, and cyberthreats on vehicles. You must be aware that automotive products are manufactured by the collaboration of various components.
Attack vector: It is a path or route that may be used by an attacker to exploit the vulnerabilities.
For e.g., if an attacker identifies a security vulnerability in one of the ECUs and exploits it, the path through which the attack occurs is called the attack vector.
Attack surface: It is an aggregate of different attack vectors or all possible points from where the hacker can exploit the vulnerability and gain unauthorized access.
For e.g., the vehicle ECU may provide a communication channel via the debug/test port for diagnostics, testing, firmware update, and routine control. Attackers can bypass the protection with vulnerabilities like weak passwords/algorithms, resulting in injecting malware or data breach. So, the attack surface, in this case, is the external debug/test port.
Now, let’s discuss the major cyberattacks in the automotive industry:
Automotive Cybersecurity- Major Cyberattacks in Automotive
In today’s rapidly evolving automotive industry, ensuring robust cybersecurity measures is paramount to protecting vehicles from potential threats and vulnerabilities. Leveraging cybersecurity consulting services, companies can better safeguard their systems against sophisticated cyberattacks. Below are some major types of cyberattacks that target automotive systems:
Denial of Service (DOS): This kind of attack is used to target a specific component of a vehicle and make it unresponsive. However, it will not give the hacker access to any of the vehicle systems. For example, an attacker with malicious intent can target a specific ECU like ABS ECU and can disable it by continuously injecting spoofed packets to disturb the normal operation. It will eventually result in the ECU becoming unresponsive. It may cause serious consequences to the driver or passengers.
Man-in-the-middle (MitM) attack: Here, an attacker manages to insert himself in the midst of the client and server, where the attacker can sniff the internal network traffic, alter the communication, spoof the client, and steal the server data.
For example, an attacker can get access to the ECU’s internal communication either via hardware or the debug interface and craft further attacks like tampering with the communication data/packets, hackers can forge the packets and make it all seem legitimate. It is possible to send proprietary messages to the ECUs to make them take some action or even completely reprogram the ECU.
Injection Attack: This attack is carried out by injecting malicious software called malware into the system. If an attacker succeeds in doing so, it can severely impact the financial, operational, and privacy aspects.
Conclusion
In the new era of the automotive industry, technology has been evolving at a great pace. However, this has increased the possibilities of cybersecurity risks that could impact the safety and security of a vehicle. To mitigate such threats, every organization should adhere to the ISO/SAE 21434 standards that provide a robust security framework for the entire development process and lifecycle of connected vehicles. These standards will evolve with technology and strict adherence will ensure success.
eInfochips is a product engineering partner for various automotive leaders across the world. Our competency spans ADAS, Infotainment & Clusters, Telematics, Connected Vehicles (V2V, V2X), EV Charging, and Multimedia Sub-systems to help global OEMs and Tier1s deliver a superior experience, safety, and efficiency. Our services and solutions range from core automotive product engineering, AUTOSAR compliant ECU software development, HMI design & testing to next-gen technology.
To know more about automotive and cybersecurity consulting services please contact us today.












