QR” is short for “Quick Response”. In this modern era, we encounter QR codes in many distinct locations including malls, small stalls, product advertisements, as payment gateways, and at many other places. Some of these codes are used for accessing websites, mobile applications, restaurant menus, making payments, placing phone calls, connecting to Wi-Fi without a password, sending emails, adding contact details, and many other functions.
Global users scanned dynamic QR codes generated by users a total of 6,825,842 times in 2022, which represents a remarkable 433% surge compared to the figures recorded in 2021.
As the above-given report suggests, QR codes have become more prevalent in recent years, and cybercriminals have also increased their phishing attacks through them. QR codes, which were originally designed for convenience, can now be used by cybercriminals to direct users to fake websites, malicious downloads, or other harmful content. Hence, it is important that users be more vigilant while using QR codes.
What is a QR Code
A QR code is a two-dimensional barcode that can be read by a smartphone or other device equipped with a QR code reader. The code consists of black and white squares arranged on a grid, and it can be scanned using a smartphone camera or a dedicated QR code reader app.
QR codes were originally developed in Japan in the 1990s to track vehicle parts during the manufacturing process. Currently, QR codes serve a diverse range of purposes, including providing a hassle-free means to disseminate information such as website links, contact details, and marketing materials.
Types of QR Codes
- Dynamic QR Code: These types of QR codes are editable, trackable, and can store a lot of information while taking up minimal space. They do not need to be recreated every time.
- Static QR code: In static QR codes, there is no flexibility to edit or change the content once it has been created.
- vCard QR code: A vCard is a replacement for a business card. Once a customer scans the card, they can view all the information about your business.
- QR Code for Restaurants: Due to the pandemic, many people have become more cautious and are taking steps to stay safe from several types of viruses. As a result, it is an innovative idea for restaurant owners to create a QR code for their menus instead of using disposable menus. With a QR code, customers can easily view the entire menu in different languages right from their fingertips.
Where QR Codes are Used by Businesses and Industries
Product Packaging
By connecting the QR code to a landing page, businesses can help customers determine the legitimacy of a product. QR codes can be used to display information about a product’s contents, ingredients, or nutritional information, without the need to open the package. QR codes can also be used to track inventory and as part of a marketing strategy to drive customers to a company website or leave a product review.
Real Estate
- Property Listings: QR codes can be used to provide information about a property for sale or rent. For example, QR codes can be placed on real estate advertisements or billboards in front of properties. When scanned, the QR code can lead to a website with more detailed information about the property, such as photos, floor plans, and a virtual tour.
- Virtual Open Houses: QR codes can be used to facilitate virtual open houses. For example, QR codes can be placed on property listings or billboards in front of properties. When scanned, the QR code can lead to a virtual open house tour or a video walkthrough of the property.
- Property Management: QR codes can be used to manage properties and track maintenance tasks. For example, a QR code could be placed on a property or on a piece of equipment, and when scanned, it could provide information about the property or access a maintenance request form.
- Leasing: QR codes can be used to streamline the leasing process. For example, a QR code could be used to access rental applications or lease agreements or to make rental payments.
QR Code Payments
QR code payments are a type of mobile payment method that enables users to make payments by scanning a QR code with their smartphone or another device. To use this payment method, a user needs a compatible smartphone and a mobile banking or payment app that supports QR code payments.
To make a payment using a QR code, the user simply scans the code using their smartphone camera or a dedicated QR code reader app. This initiates the payment process and transfers the funds from the user’s bank account or payment account to the merchant.
QR code payments are becoming increasingly popular due to their speed, convenience, and security. They are easy to use, as they do not require the user to enter sensitive information such as credit card numbers or passwords. QR code payments are also contactless, allowing them to be made without physical contact between the user and the merchant.
Healthcare
QR codes can be used to identify patients and access their medical records. For example, a patient could receive a QR code that can be scanned to gain access to their Electronic Health Record (EHR) or other medical data.
QR codes can also be employed to monitor and control medicine consumption. For instance, a patient may be given a QR code to scan when taking their medication, which can help healthcare providers monitor their medication adherence and potential side effects.
In hospital settings, QR codes can be used to prevent the transmission of illnesses. For example, a QR code could be used to track the cleaning and disinfection of equipment or to access guidelines for preventing the spread of infections.
How QR codes work
QR and barcodes work similarly. Each black square and dot represent different information. When we scan the QR with a QR reader or scanner, its pattern converts to human-readable data.
Numerous types of information, including text, URLs, and other data, can be encoded using QR codes. They are frequently used to link to websites or other online resources or to allow rapid access to information. QR codes can be found on everything from business cards and billboards to packaging and product labels.
Criminal hackers can use QR codes to create phishing attacks
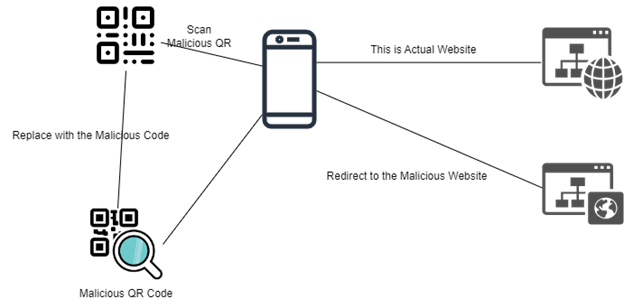
Criminal hackers can use QR codes to create phishing attacks in several ways. One method is by creating a fake QR code that looks legitimate and placing it in a public location, such as on a billboard or in a store. When someone scans the code, it could lead to a website that looks like a legitimate login page or other online service but is fake and designed to steal the user’s login credentials or personal information.
Another way that hackers can use QR codes for phishing attacks is by sending a message or email that includes a QR code that, when scanned, leads to a fake website or downloads malware onto the user’s device.
Different Types of Hacking QR codes
- Malicious QR codes: Hackers can create QR codes that, when scanned, lead to malicious websites that can infect the user’s device with malware or phishing scams.
- QR code spoofing: Hackers can create fake QR codes that look legitimate but lead to malicious websites or other content. This can be done by altering the appearance of the QR code or creating a code that looks like a legitimate QR code.
- QR code tracking: Hackers can use QR codes to track the movements and activities of users who scan the codes. This can be done by embedding a tracking code in the QR code or using the code to redirect users to a website that collects data on their activities.
Mitigation of QR Attacks
- Only scan QR codes from trusted sources: Be careful about which QR codes you choose to scan. If you are not sure whether a QR code is from a trusted source, it is best not to scan it.
- Check the URL: Before scanning a QR code, you can check the URL that it encodes by using an online QR code scanner. This can help you identify malicious QR codes that are designed to redirect you to a malicious website.
- Use a QR code scanner app: Instead of using the built-in QR code scanner on your smartphone, consider using a QR code scanner app that has additional security features. Some QR code scanner apps can alert you if the QR code you are about to scan is suspicious or potentially malicious.
- Use a VPN: If you are concerned about your online privacy and security, you may want to use a Virtual Private Network (VPN) when accessing the Internet. A VPN can help protect your data and prevent hackers from tracking your online activities.
- Enable two-factor authentication: Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring you to provide a second form of authentication, in addition to your password, when logging in. Consider enabling 2FA on your important accounts to make it more difficult for hackers to gain access.
Wrapping Up
QR codes have become ubiquitous in modern times and are used in many ways, such as product packaging, real estate, healthcare, and even as a form of mobile payment. However, with their increased usage, cybercriminals have begun using them for phishing attacks, directing unsuspecting users to fake websites or malicious downloads. It is essential that users remain vigilant when scanning QR codes and take steps to verify their legitimacy. Overall, QR codes offer a convenient and versatile method for sharing information, making payments, and streamlining business processes, but users should be aware of the potential risks associated with their use.
iOS penetration testing is an advantageous process for businesses that plan to publish or already have an iOS application. Working with a security-specialized business improves data protection. Even minor code errors may lead to security breaches and data loss. Vulnerability assessment and penetration testing help identify and mitigate potential attacks. This offers a surface-level analysis of the application security posture.
We help enterprises design, implement, and manage security products at all device-connectivity-application levels. We follow industry security standards like NIST, ENISA, OWASP, MITRE, and IoT Security Foundation. Our cybersecurity experience encompasses devices, OS/firmware, web/mobile apps, data, and cloud workloads.
eInfochips provides strategic evaluations, transformations, full implementation, and managed security operations. Our cybersecurity engagements follow industry security standards. Contact our infosec specialists for more information about our cybersecurity testing services.