The Radio Equipment Directive (RED) 2014/53/EU sets essential requirements for radio equipment entering the European Union by traditionally focusing on the spectrum of use and safety standards. The Radio Equipment Directive experienced significant development with its enhanced cybersecurity considerations presented in Articles 3.3(d), (e), and (f).
The directive mandates articles that aim to protect against unauthorized access while preserving privacy and preventing misuse of networks. As connected devices such as smart bands and IoT gadgets become widespread, the security of these radio-connected products becomes pivotal.
For manufacturers seeking expert support, our RED compliance and cybersecurity services offer end‑to‑end guidance, from design review and threat modeling to testing and CE marking.
This blog demonstrates how manufacturers and developers should integrate cybersecurity within the design phases of radio equipment to achieve compliance with the RED and protect against new threats. It also details the essential design principles together with practical implementation strategies and documentation requirements which enable a secure-by-design methodology.
Introduction
With the digital revolution, we are in an era of hyper-connectivity, where devices such as fitness bands and medical wearables frequently communicate through wireless interfaces like Bluetooth, Wi-Fi, NFC, and cellular modes. This connectivity is enormously convenient, but it also exposes new attack surfaces. Once compromised, a vulnerable device can be co‐opted, hacked, or otherwise abused to exfiltrate sensitive data, leaving end-users and networks vulnerable.
In recognition of this emerging threat, the European Union amended the Radio Equipment Directive (RED) to require cybersecurity requirements for internet connected equipment. In particular, Articles 3.3(d), (e) and (f) require safeguards against unauthorized access, breach, or accidental loss.
To comply with these requirements, manufacturers must shift from a reactive security posture to a proactive, integrated approach starting from the very first design sketch of their products. This blog explains how to embed cybersecurity in radio equipment design from a RED perspective and provides practical insights into the technical and regulatory implementation.
Understanding the RED’s Cybersecurity Requirements
The RED is the foundational legislation for any devices emitting radio waves, sold in the EU market. Starting August 2025, Articles 3.3(d/e/f) will be applicable to the following classes of connected devices:
- Wearable tech and smart bands
- Connected mobile toys
- IoT products (smart home devices, for example)
- Appliances that connect to networks
- Article 3.3(d): Protection from Unauthorized Access: Devices must be engineered such that their radio network or other associated networks cannot be hacked into.
- Article 3.3(e): Protection of Personal Data and Privacy: Devices must have mechanisms that will ensure privacy and personal data of the user is not violated.
- Article 3.3(f): Protection Against Fraud or Misuse: Devices are expected to ensure that there is no abuse of network resources including fraudulent use of communications and service denial.
Standards EN 18031 – Regulations on Cybersecurity
According to the EN 18031 standards, an “asset” is defined as a vital element or function that must be protected. They set several criteria which must be met by the final manufacturers. These criteria fall within these specific domains:
- Access Control Mechanism: The device should have the appropriate control mechanisms that restrict access to security and network assets to authorized entities only.
- Authentication Mechanism: Access to read, modify, or use configuration of network functions and security parameters should be restricted through a controlling mechanism.
- Secure Updates: The installation of new software must maintain integrity and authenticity; thus, a secure update mechanism must be in place.
- Secure Storage Mechanism: The mechanism should protect the confidentiality and integrity properties of the assets.
- Secure Communication Mechanism: The mechanism protects the communication of assets from disclosure and ensures authenticity, confidentiality, and anti-replay properties.
- Resilience Mechanisms: Functions and practices that help improve operational resilience to denial-of-service (DoS) attacks through network interfaces.
- Monitoring Mechanism: This is the system to monitor and detect DoS attacks targeted at network traffic.
- Traffic Control Mechanism: This system identifies and detects malicious behaviors in network traffic.
- General equipment capabilities: They optimize operational and technical practices to enhance vulnerability management by reducing the attack surface and leveraging the security-by-design principles.
- Cryptography and the management of private cryptographic keys: The majority of the recognized international cybersecurity standards are applicable to cryptography. The BSI TR-02102-1, SOGIS Agreed Cryptographic Mechanisms, ETSI TS 119 312 and NIST SP 800-57 all provide relevant international standards.
Process Flow of the Radio Equipment Directive (RED)
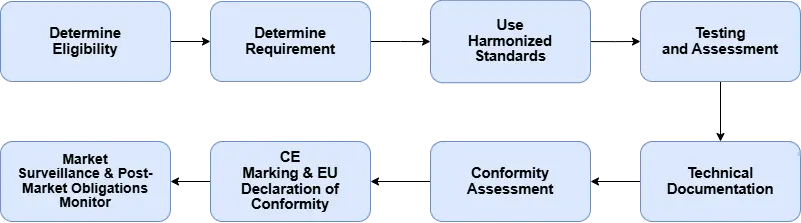
Figure.1 The RED Process Flow
1. Determine Eligibility
- Confirm if the device is within the scope of the RED (i.e., it emits or receives radio waves)
- Common Types of Technology: Bluetooth, Wi-Fi, LTE/5G, RFID, NFC, Zigbee, etc.
2. Determine Requirement
- Requirements under RED must now be satisfied by the product.
- Article 3.1(a): Health and Safety (e.g., EMF exposure)
- Article 3.1(b): EMC (Electromagnetic Compatibility)
- Article 3.2: Efficient use of the radio spectrum
- Article 3.3 (Optional unless required):
- (d) Protection against unauthorized access
- (e) Protection of personal data and privacy
- (f) Protection against misuse or fraud
- Articles 3.3(d/e/f) become mandatory from the 1 August 2025 but will apply only to specific categories (e.g., wearables, toys, IoT etc.).
3. Use Harmonized Standards (if available)
- Use standards published in the Official Journal of the EU (e.g., ETSI EN 300 328, EN 301 489, EN 303 645). This provides a presumption of conformity.
4. Testing and Assessment
- Required RF performance testing for EMC and safety testing for cybersecurity (e.g., authentication, data protection, secure updates). Use either internal testing or accredited laboratories also called Notified Bodies or NBs.
5. Technical Documentation
- Produce and maintain a technical file with, but not limited to, product description risk assessment test reports, circuit diagrams, schematics, software/firmware cyber security mechanisms, Declaration of Conformity (DoC).
6. Conformity Assessment
- Self-assessment (Module A) if all the Harmonized Standards have been used.
- Use a Notified Body if one has used or only partially used a Harmonized Standard (Modules B+C or H).
7. CE Marking & EU Declaration of Conformity
- Affix the CE marking on the product in a visible, durable manner.
- Provide the EU Declaration of Conformity with the product (in digital or paper format).
8. Monitor Market Surveillance and Post-Market Obligations of Product Use
- Report safety incidents or non-conformities.
- Keep a record of traceability of production.
Leveraging Product Security Platforms for the RED Cybersecurity Compliance
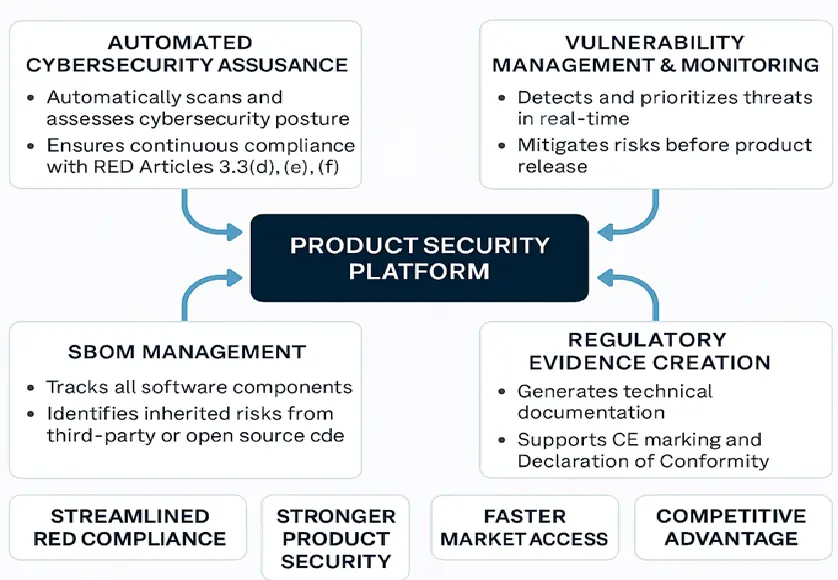
Figure 2. Product security with RED compliance
There is an increasing urgency for product manufacturers to produce secure-by-design products, with the Radio Equipment Directive (RED) increasing the stringency, especially as Articles 3.3(d), (e), and (f) are now mandatory for most connected devices. To do this effectively, they rely on advanced product security platforms.
1. Automatic Cybersecurity Confidence
One cannot just check a box and declare the product as compliant with the RED. Compliance requires constant risk analysis and threat mitigation. Some platforms automate all these actions for a constant view of a product’s cyber-security posture, minimal manual effort, and consistent compliance across the product lifecycle.
2. Managing Vulnerabilities in Real-Time
It is important to highlight and correct any issues promptly to prevent expensive recalls or regulatory issues. Real-time monitoring and prioritization empower manufacturers to discover, prioritize and fix vulnerabilities long before they are exploited in a cyber-attack.
3.Software Bill of Materials (SBOM) Transparency
The RED compliance and supply chain security, for that matter, require all software to be fully visible. It simplifies SBOM creation and management, helping teams understand where the vulnerabilities lie and ensure full transparency of any third-party and open-source software use.
4.Automated Compliance Documentation
Generating regulatory evidence can be time-consuming and error prone. Automating the creation of technical files, risk assessments, test reports, and EU Declarations of Conformity saves time, reduces errors, and makes audits more manageable.
Conclusion
As connected devices become embedded in every aspect of life, the integration of cybersecurity into the design of radio equipment has evolved from being optional to being critical. The EU’s Radio Equipment Directive, with its provisions regarding cyber security with sections Articles 3.3(d), (e), and (f), is changing the way manufacturers think about product development.
Manufacturers can apply security-by-design, show compliance using standards such as ETSI EN 303 645, and consider the compliance deadline of August 2025. In the end, security-by-design is not just about consumer safety and privacy; it also encompasses the long-term resilience and reputation expansion opportunities for industrial brands within the EU and the global consumer markets.
The importance of cybersecurity for radio devices is now an integral aspect of regulatory compliance under the Radio Equipment Directive (RED). It is important for manufacturers to implement solutions that provide protection while facilitating the certification process. Product security platforms enable businesses to address these new challenges by automating security assurance, handling vulnerabilities, managing the Software Bill of Materials (SBOMs), and creating regulatory papers with accuracy. By incorporating a solution platform like this into their toolkit, manufacturers can now develop secure, compliant products without compromise; thereby delivering products to market quickly, more intelligently and with fortified resilience against cybersecurity threats.











