The Software Development Life Cycle is a concept that describes the elements of application development and the sequence in which they must be accomplished. It consists of several phases that offer a step-by-step method for gathering requirements, designing, implementing, testing, and delivering software. Every component of the SDLC generates outputs necessary for the succeeding phase of the life cycle. Within the boundaries of time and money, the main objective of the SDLC is to regulate the development process and generate high-quality software that satisfies the client’s requirements.
Over the years, a wide range of models have emerged based on this framework, each with its own set of known pluses and minuses. Some of these models include Waterfall, Spiral model, V-Model, Incremental model, and Agile model. The International Organization for Standardization (ISO) standard on system and software development, ISO/IEC 12207, defines the software development procedure as a structured collection of activities necessary to build a software product.
What is Secure SDLC?
The Secure Software Development Life Cycle (SSDLC) is a process that provides a framework for developing secure software. This procedure is applicable to any kind of software development project. To develop and deploy a secure application, a series of tasks known as the Secure Software Development Life Cycle must be carried out. Secure SDLC takes a shift-left approach to incorporating security practices from the start of the project or SDLC.
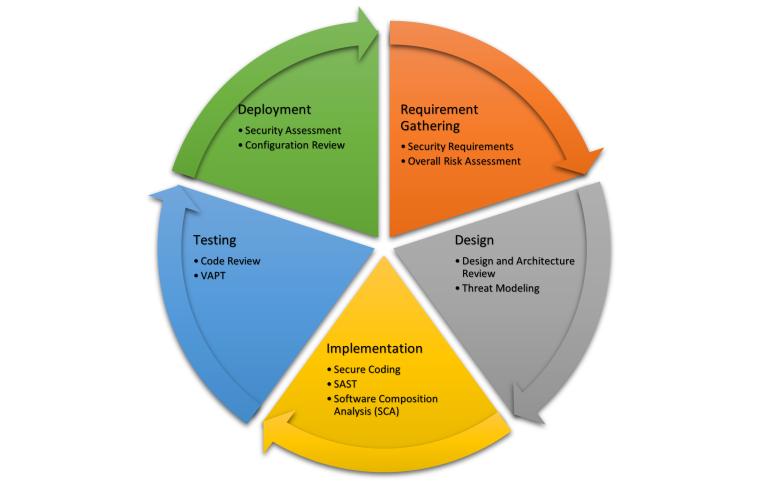
These activities can be divided into five phases
- Requirement gathering
- Design
- Implementation
- Testing
- Deployment
These phases may sound like SDLC phases, but activities performed in these phases are an addition to the normal SDLC activities.
The goal of the Secure SDLC is not to totally replace conventional security procedures like penetration tests, but rather to integrate security into the development process and provide security-related processes and guidance to create secure applications.
Importance of Secure SDLC
The current market trend is to perform vulnerability assessments on finished products and then fix any issues found during those assessments. Testing, patching, and retesting can involve several iterations and cost businesses money. By addressing these security concerns earlier in the SDLC, they can be avoided.
There was a time when businesses only cared about developing applications and selling them to customers, ignoring other challenges. Those days have passed. The threat landscape has drastically changed.
Nowadays, there are cybercriminals and hackers who intend to break into computer systems and networks to obtain data, money, or simply for fun. Some of them break into systems just to gain fame on the internet. These incidents can result in significant losses for organizations, including monetary loss, trust loss, or data loss. Organizations will undoubtedly suffer losses in the end.
Instead, organizations can invest money in cybersecurity to protect their assets from any kind of breach. This is where the Secure SDLC comes into play. Businesses can hire ethical hackers and implement processes like S-SDLC (Secure Software Development Life Cycle) to address the above-discussed issues in a cost-effective manner by identifying security issues earlier in the development life cycle.
By tackling these issues early in the development process, organizations can decrease the total cost of their apps. If problems are discovered later in the SDLC, the cost of development to fix them may increase by 100 times.
Secure SDLC Explained in detail
The secure software development lifecycle (SSDLC) involves incorporating security activities in each phase of the SDLC. Rather than having a separate “security phase,” there is a set of rules, best practices, and tools that can be integrated into the SDLC’s conventional phases. The following explanation provides an overview of each phase and its associated security activities. This is a basic understanding, and additional or deleted steps may be required depending on specific project requirements.
Requirement gathering
In this initial phase, requirements for new features are gathered from different participants. During this phase, security considerations (security requirements) should also be gathered. After that, an overall risk assessment should be done for the requirements.
Activities in this phase
- Security considerations for given functional requirements
- Overall risk assessment
Design
The design phase uses the functional and security requirements finalized in the requirement gathering phase. This phase defines the software architecture and design considering both functional and security requirements. Functional requirements specify what should happen, while security requirements specify what should not happen.
Activities in this phase
- Design review
- Threat modeling
Implementation
In the implementation phase, the actual implementation of the product’s functional and security requirements takes place. This phase also involves developing security procedures and policies and applying security mechanisms using secure coding best practices. If these mechanisms are not applied appropriately, the software will be susceptible to attacks.
Activities in this phase
- Secure coding best practices
- Static Application Security Testing (SAST)
- Software Composition Analysis (SCA)
Testing
During this phase, testing helps to identify software vulnerabilities and ensure that the security mechanisms are effective. Potential security threats are also addressed during this phase. Iterations of testing are carried out to confirm that the system is free of well-known vulnerabilities. These testing iterations may include automated security testing tools or manual security testing based on the product requirement. This phase is crucial to the success of the SSDLC.
Activities in this phase
- Code review
- Vulnerability assessment & penetration testing (manual/automated)
Deployment
In the Secure Software Development Life Cycle, the deployment phase is critical. This is the phase where the product is deployed and used in the production environment. It is also the phase in which all security controls defined throughout the design and development phases are tested. Along with all the security measures, configurations of the deployment environment are also checked to ensure the secure development of the product. Therefore, having a well-defined and well-implemented deployment strategy is crucial.
Activities in this phase
- Security assessment
- Configuration review
How eInfochips can Help Integrating Security in SDLC?
To ensure the secure development of our clients’ products, eInfochips offers comprehensive solutions. Depending on requirements, we incorporate a range of security best practices into the software development lifecycle using DevOps services. Our approach integrates Secure-by-Design and Defense-in-Depth strategies, following the Secure SDLC methodology to safeguard products right from the design phase of development.
Our security workflow includes many things, from requirement gathering to Secure-by-Design and vulnerability assessment and penetration testing and can be aligned with the product development life cycle. This strategy ultimately helps customers deploy secure products in an open world, allowing products to be secured with multi-layered security.
eInfochips provides both development and security services, in which we implement a Secure Software Development Life Cycle with the best security activities and procedures. eInfochips’ expert resources provide IoT (Internet of Things) and cybersecurity services with the great expertise gained during their many years of experience in the domain.
We offer cybersecurity expertise for threat modeling and VAPT (Vulnerability Assessment and Penetration Testing) spanning cloud, OS/firmware, web/mobile apps, data, and devices that meet the standards of the cybersecurity industry (such as IEC/ISA-62443, HIPAA, GDPR, Open Web Application Security Project), regulations, and recommendations (like MITRE, National Institute of Standards and Technology, Open Web Application Security Project, IoT Security Foundation, and ENISA).