Introduction
As energy systems become more connected and software-driven, cyber threats targeting Battery Management Systems (BMS), electric vehicles, and critical infrastructure are rising. There are several incidents of such attacks, from battery manipulation to large-scale disruptions.
Following are some incidents related to Electric Vehicle (EV) batteries, the charging infrastructure, and the energy grid which shows the urgent need to implement a stronger security in the battery ecosystem and BMS in general:
- NREL EV Battery Vulnerability (2021): Researchers found that hackers could remotely alter the EV battery performance, causing system failures and overheating risks.
- Colonial Pipeline Ransomware Attack (2021): Hackers shut down the critical energy infrastructure, demonstrating how ransomware attack could damage battery-powered grids.
- EV Cybersecurity Attacks (2018-2021): There has been an astonishing increase of 225% in attacks targeting EVs and charging stations between 2018 to 2021, causing grid overloads, remote shutdowns, and battery manipulation.
Cybersecurity is essential for BMS
A BMS (Battery Management System) is the main system of any energy storage system. It is responsible for various critical functions such as battery health monitoring, managing charging/discharging cycles, maintaining thermal stability, balancing cell voltages, and enabling remote diagnostics. As the connectivity for remote monitoring increases, the BMS becomes the first target for cyber threats.
Why is it essential to secure the BMS?
There are several following reasons for that:
- Battery Safety & Performance Risks – Unauthorized access can change charge/discharge rates, leading to overheating, thermal runaway, or permanent damage.
- System Downtime – Attacks can damage BMS functionality, which results in system shutdowns or operational failure in the applications.
- Data Breach – Hackers can steal energy consumption data, and user specific information to create havoc.
- Ransomware Attacks – Attackers can exploit vulnerabilities to lock the BMS system and demand ransom to restore the access.
- Supply Chain related Security Risks – Compromised firmware can make an entire fleet of vehicles or energy storage units vulnerable.
Types of cyber-attacks on a BMS There are the most common types of cyberattacks that can target and exploit a BMS:
- Denial of Service (DoS) Attacks – An attempt to overload a system to disrupt battery monitoring and control.
- Man-in-the-Middle (MITM) Attacks – A cyberattack where a hacker can intercept and tamper with communication system of the BMS components.
- Firmware Tampering – Unauthorized modification or inserting malicious firmware updates to change BMS functions.
- Unauthorized Remote Access – Remotely taking control of a BMS due to poor authentication.
- Fuzzing: Attackers can send random inputs to the BMS software to identify vulnerabilities, which leads to crashes, data corruption, or unauthorized access.
- Fault Injection: Hackers can manipulate voltage, temperature, or electromagnetic signals to disrupt normal BMS operations, which can cause incorrect parameter readings, unscheduled shutdowns, or even thermal runaways.
The main cause for BESS (Battery Energy Storage System) failure in 2023 was the system design and integration. The image below represents the root cause for a BMS failure in a BESS system over the period 2018 to 2023.
Root Cause trend over time
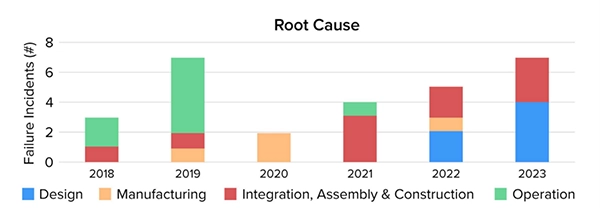
Image Source: Insights from EPRI’s Battery Energy Storage Systems (BESS) Failure
Key Components of BMS and Cybersecurity Focus Areas
A BMS has various important hardware and software components like a battery management unit, a cell monitoring unit, a battery junction box, algorithms, etc., all of which require specific cybersecurity measures.
Cybersecurity can be implemented at various levels of the BMS architecture to mitigate risk effectively:
- Battery Management Unit (BMU): Secure communication channels, firmware integrity checks, and cryptographic authentication.
- Microcontrollers (MCUs): Secure boot, encrypted firmware updates, and hardware-level authentication.
- Gateways: Firewall protections, intrusion detection, and encrypted data transmission.
- Cell Monitoring Unit (CMU): Secure sensor data encryption and anomaly detection
- Cell Modules: Secure data logging, firmware validation, and periodic security audits.
- State-of-Charge (SoC) and State-of-Health (SoH) Algorithms: Secure software algorithms to prevent unauthorized data manipulation.
Key security measures for BMS
There are many important measures which can enhance the security of BMS. These measures can be implemented at different layers of the BMS system by:
1. Securing Communication & Data Integrity
- Implementing end-to-end encryption (AES-256, TLS 1.3) to secure data transfer between BMS and cloud systems.
- Applying cryptographic authentication to all firmware updates and preventing malicious modifications.
- Using secure communication protocols such as MQTT and HTTPS for remote monitoring and control.
2. Strengthening Access Control & Authentication
- Multi-Factor Authentication (MFA) can be implemented for all remote BMS access points.
- Role-Based Access Control (RBAC) can be used to restrict data access based on users defined roles.
- Digital signatures can be used for the verification of firmware updates.
3. Intrusion Detection & Anomaly Monitoring
- An AI-based anomaly can be used to identify deviations in battery behavior that could indicate cyberattacks.
- A real-time intrusion detection system (IDS) can be used for network traffic analysis.
4. Securing Network Interfaces & Connectivity
- Isolate the BMS networks from public networks using firewalls and VPNs.
- Use a secure API gateway to monitor and validate third-party interactions.
- A regular penetration testing can be done to mitigate security vulnerabilities.
5. Firmware & Hardware Security Enhancements
- Secure boot mechanisms can be used to make sure that only authorized firmware runs on the BMS.
- A hardware security module (HSM) can be integrated for storing cryptographic keys securely.
Design considerations for a Cyber-Resilient BMS
eInfochips has helped various companies in designing, developing, and managing secure, connected products across the device, connectivity, and application layers. We have a team of certified experts with strong experience in security standards and provide comprehensive security solutions supported by a dedicated cybersecurity lab for VAPT.
Following are the areas where eInfochips can help companies in implementing a cyber-attack resilient BMS system:
1. BMS Security Assessment
- BMU & CMU Security – Identify firmware vulnerabilities, secure real-time data, and prevent false SoC/SoH reports.
- Gateway & Network Security – Secure CAN, Modbus, MQTT, OPC-UA.
2. Security by design
- Hardware Security – Secure bootloaders and encrypted firmware storage.
- Secure Communication – Use AES-256, TLS 1.3, certificate-based authentication for BMS-to-cloud/vehicle connectivity.
- Data Integrity – Tamper-proof logs & cryptographic SoC/SoH validation.
3. Secure Firmware & OTA Updates
- Encrypted OTA Updates – Secure firmware with digital signatures & rollback protection.
- AI-Powered Threat Detection – Identify abnormal firmware behavior & isolate threats.
4. Managed Cybersecurity Services
- Threat Monitoring & Response – Anomaly detection, automated alerts, 24/7 security monitoring.
- Regulatory Compliance – ISO 21434, IEC 62443.
- BMS Penetration Testing – Identify & fix firmware, hardware, and network vulnerabilities.
Conclusion
Electric Vehicles and Energy Storage systems are growing, so it is critical to secure BMS system. Cyber threats on BMS are rising therefore it is important to implement strong security measures such as encryption, secure firmware updates, and anomaly detection. These measures can protect the performance and integrity of battery ecosystems from unwanted access and manipulation.
eInfochips supports various customers in designing secure hardware, firmware and software systems with dedicated SMEs and cybersecurity labs. Our proven track record in EV, grid storage, and industrial BMS ensures a secure and resilient infrastructure, helping companies safeguard their critical energy systems.













